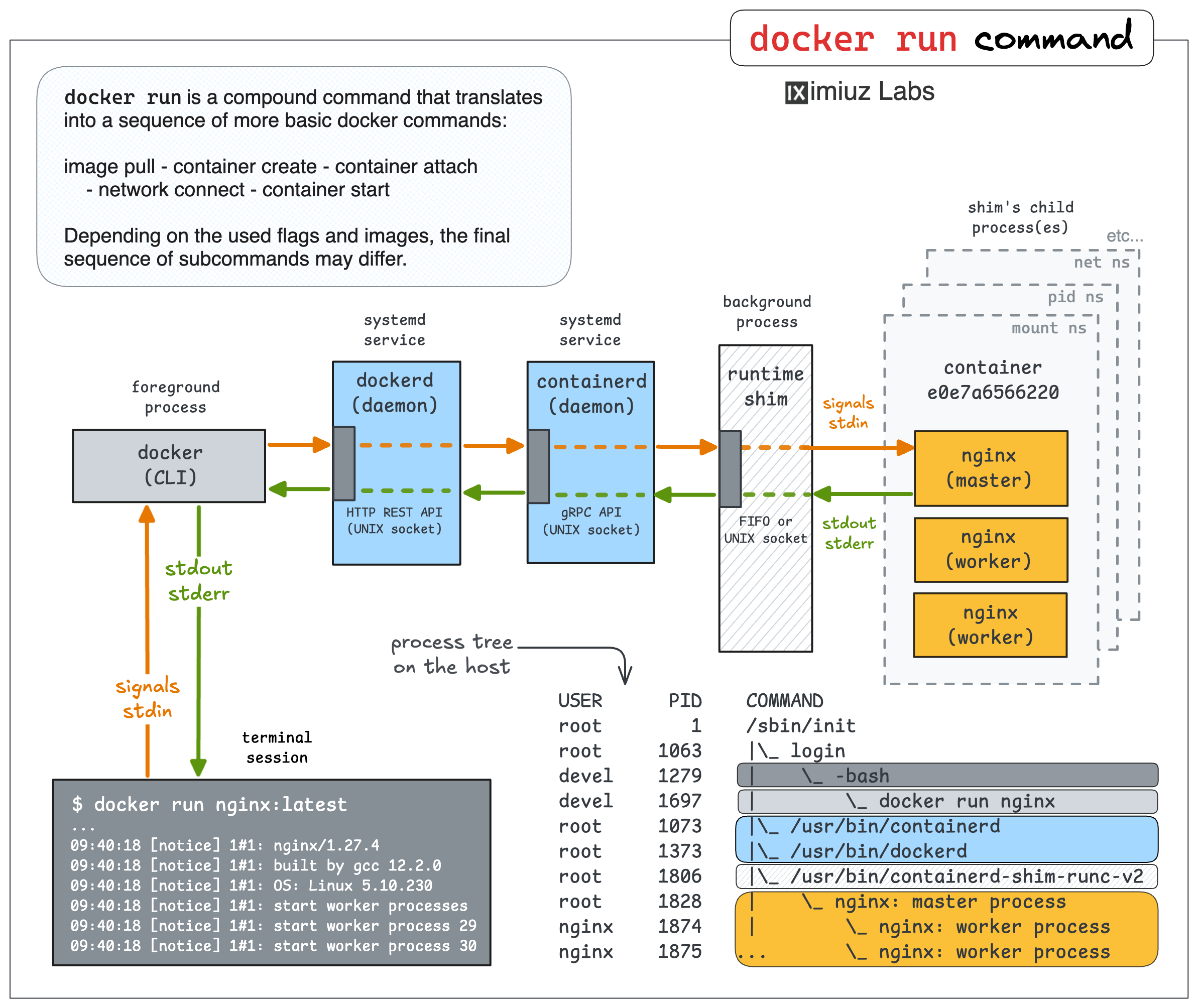
Docker Run, Attach, and Exec: How They Work Under the Hood (and Why It Matters)
Dive into the internals of the Docker run, attach, and exec commands by following this highly visual and hands-on tutorial.
Explore tutorials, challenges, courses, and more published by this author.
Dive into the internals of the Docker run, attach, and exec commands by following this highly visual and hands-on tutorial.

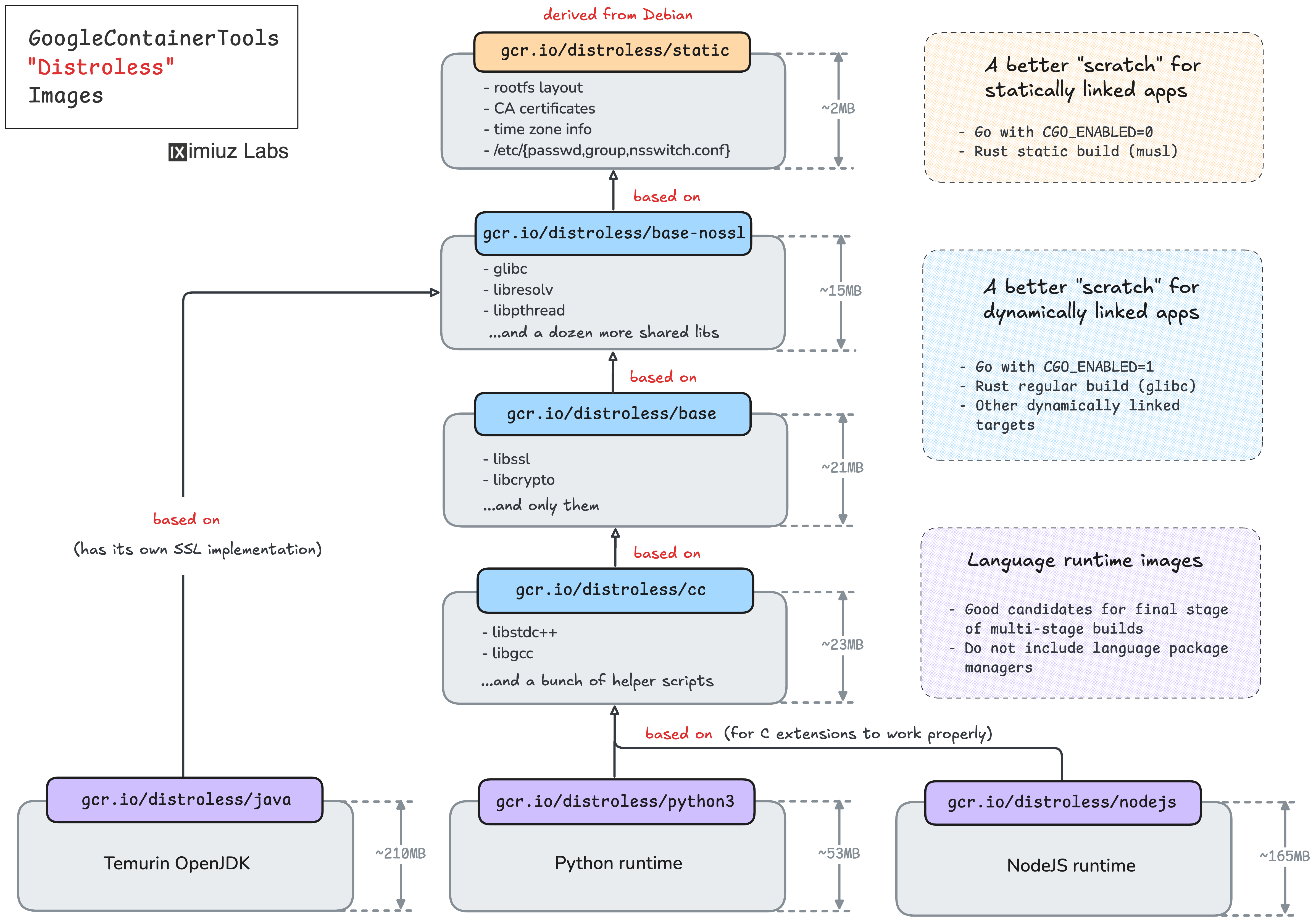
What are these distroless images, really? Why are they needed? What's the difference between a container image built from a distroless base and a container image built from scratch? Let's take a deeper look.
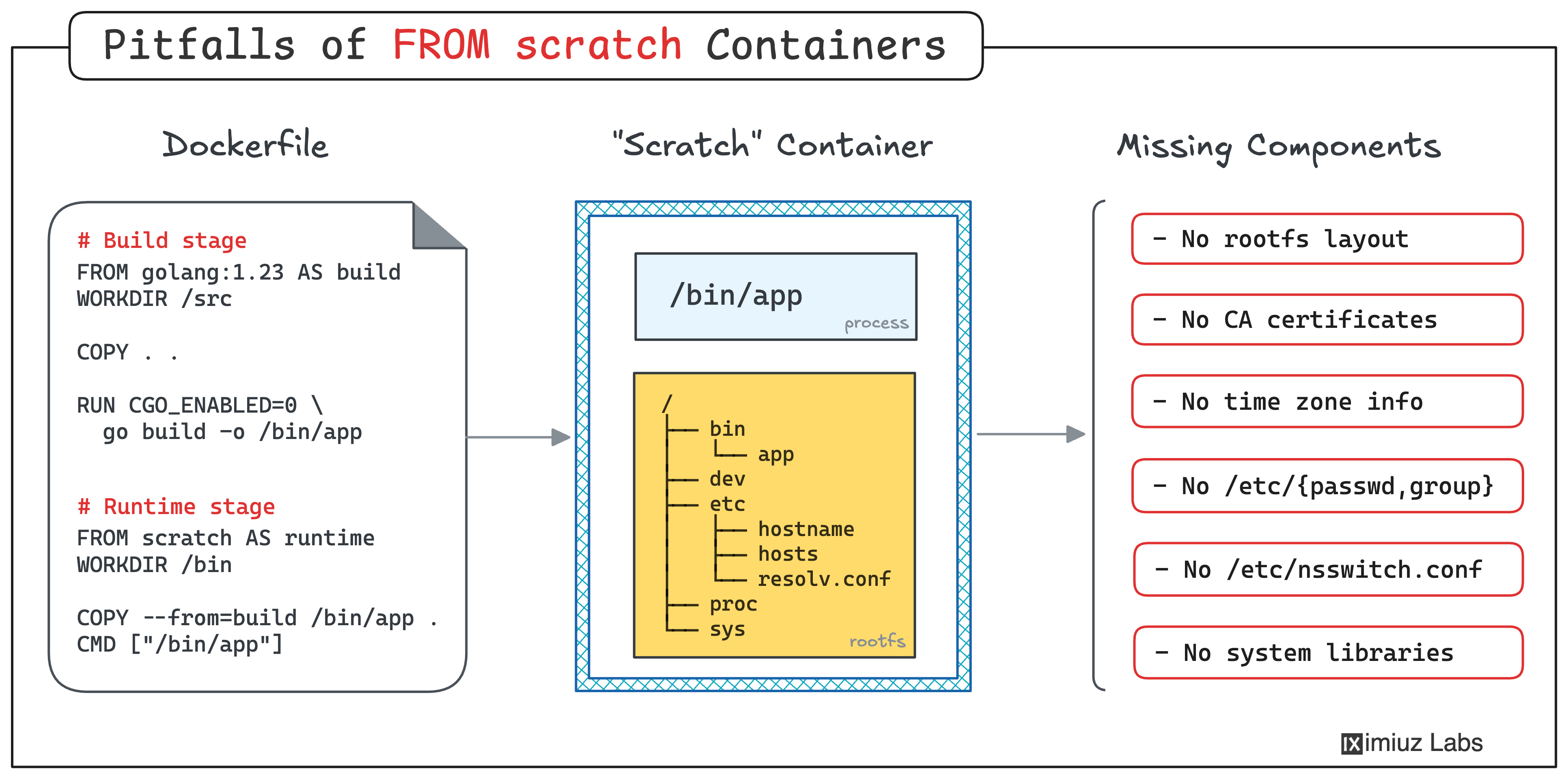
While "FROM scratch" containers may seem functional, they often lack essential components that programs expect to find in their execution environment. Discover the most common pitfalls of building container images "FROM scratch" and learn how to avoid them.
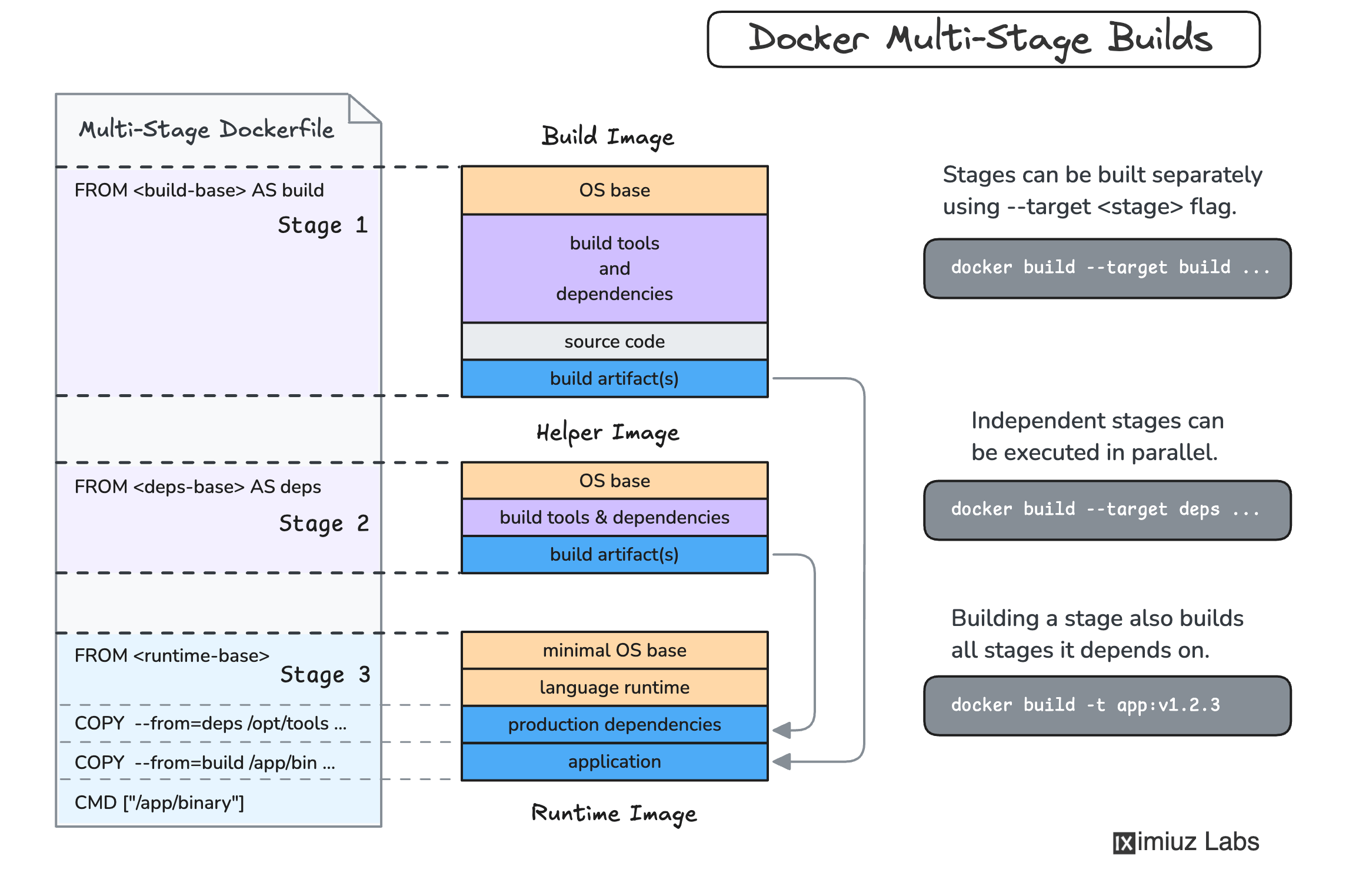
Learn how to build smaller, more secure Docker container images using Multi-Stage Builds. This guide explains common sources of image bloat, best practices for slimming down production images, and practical examples for Node.js, Go, Rust, and other application stacks. Start optimizing your containers today!
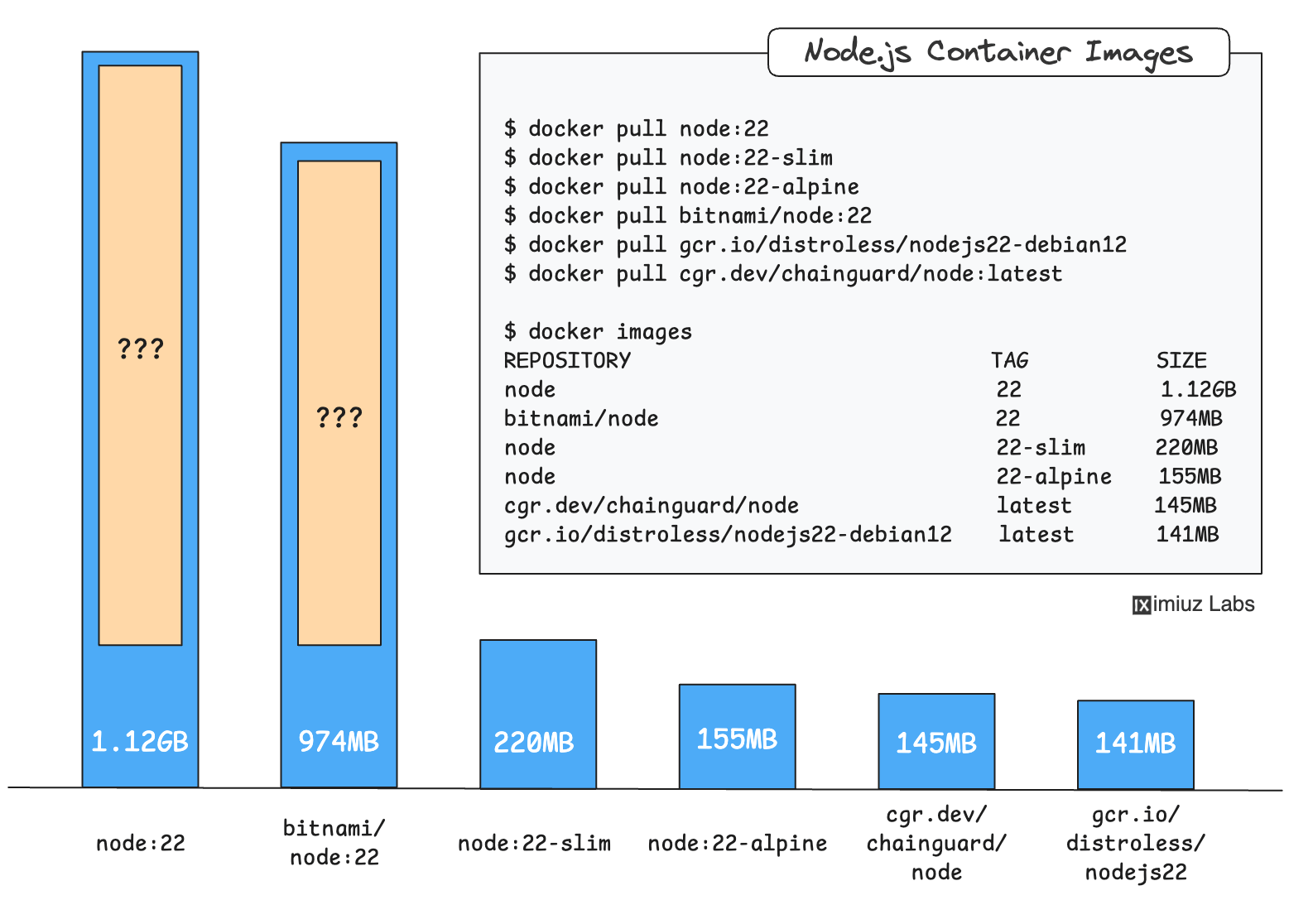
Choosing the right base image for your Node.js application can drastically affect its security, size, and performance. This post breaks down popular options - from slim and distroless to full-sized images - helping you navigate the trade-offs and pick the best fit for your development, build, and production needs.
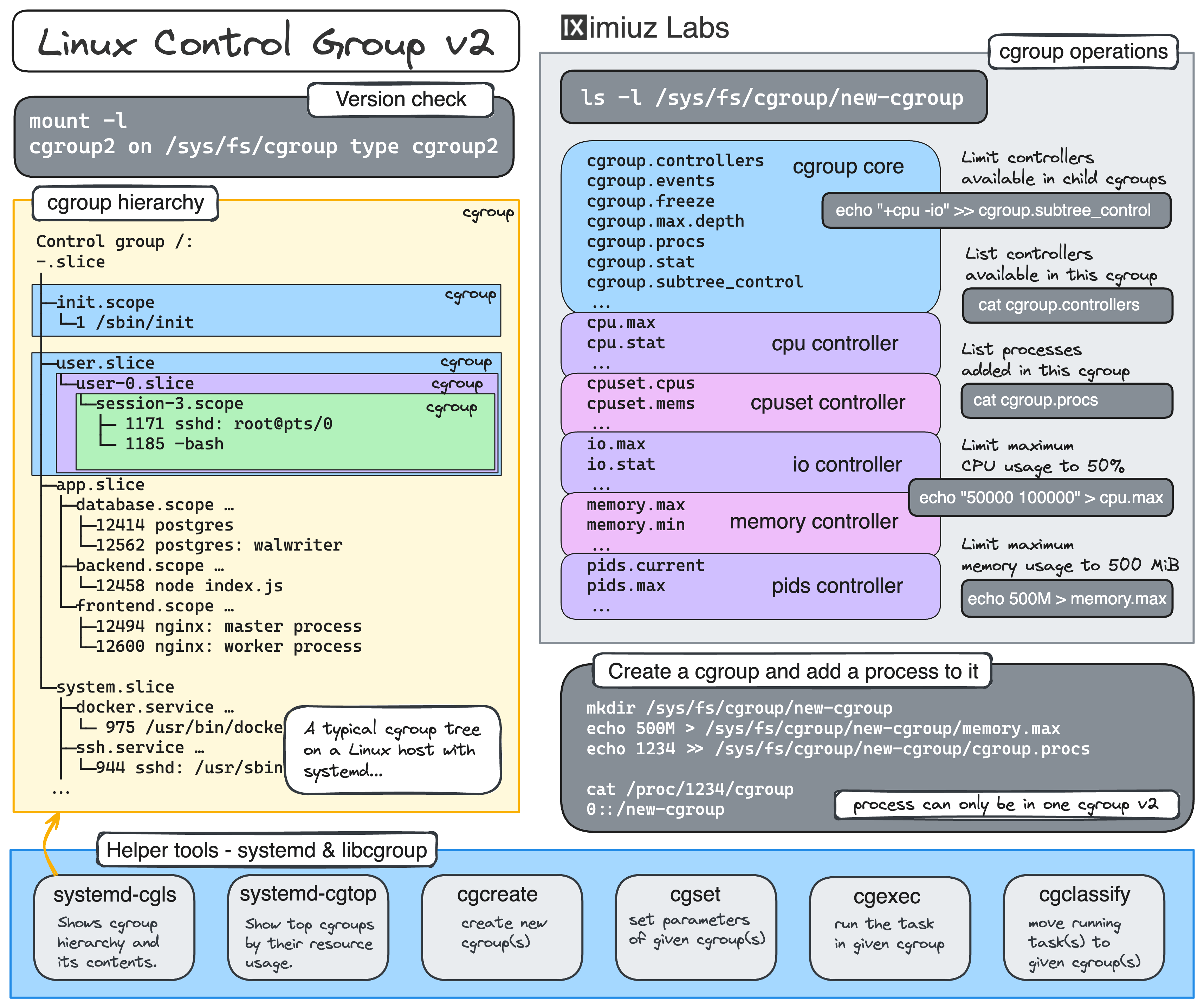
Learn how to limit process resources using Linux cgroups - from the most basic and labour-intensive cgroupfs manipulation to the handiest systemd-run command.
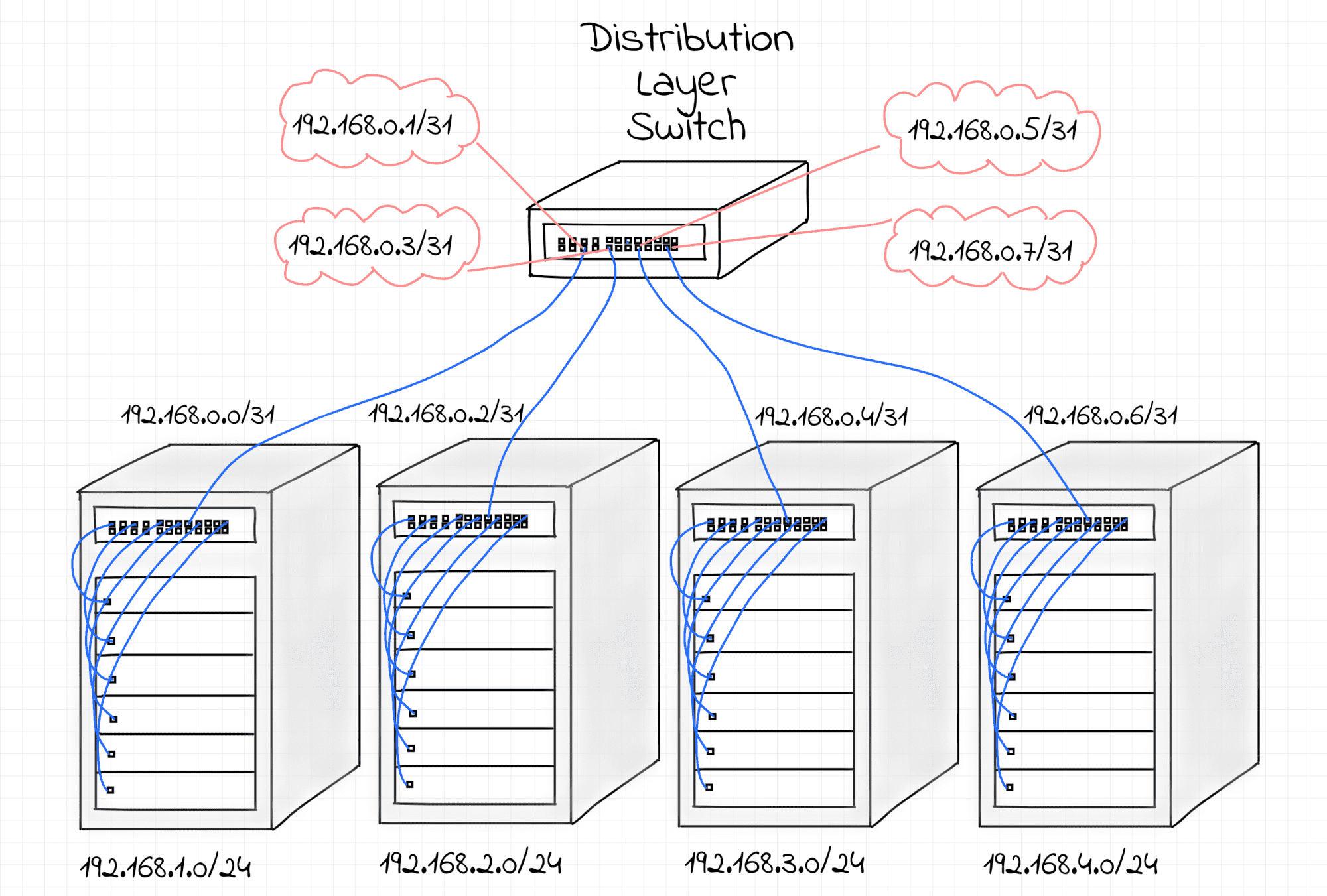
The culmination of the Docker networking challenges series. Can you create a Docker-like bridge network from scratch and using nothing but basic Linux commands.
Prove your Linux networking skills by connecting two network namespaces with a virtual Ethernet device.
Prove your mastery of Linux and containers by connecting multiple network namespaces into a single network.
There is a container that seems to have access to all host's interfaces but for some reason cannot call any addresses outside of the host. Can you fix it?
Learn how to create fully isolated virtual network environment using Linux network namespaces.
Learn how to tag and push container images to a remote registry using the ctr command.
A heavily illustrated introduction to the first two layers of Computer Networking: Ethernet and IP. A must for any developer or DevOps engineer who wants to build solid understanding of computer networking before they move to the higher-level protocols like TCP, UDP, and even HTTP.
Build a mental model of how Dagger works by migrating an example software project from traditional script-based automation to a Dagger-powered development workflow, peeking under the hood of the new technology on the way.

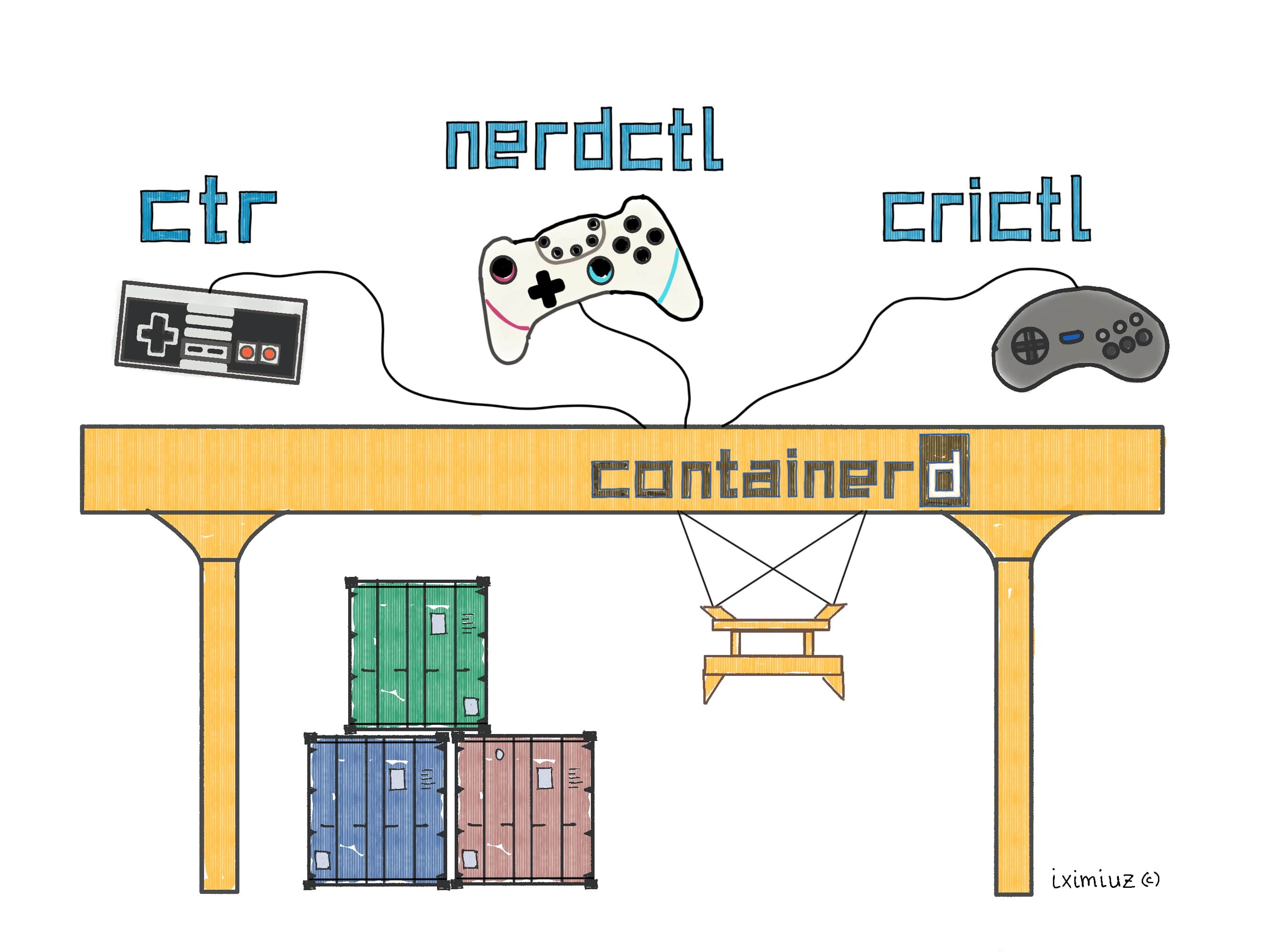
Explore containerd with ctr, its default command-line client, try nerdctl as a potential Docker alternative, and learn how to debug Kubernetes Pods with crictl.
Go from zero to a confident Docker beginner. Learn how to run containers of all kinds, interact with them, and build a clear mental model of how Docker manages your applications behind the scenes.
Explore how different container runtimes - Docker, Podman, nerdctl, ctr, and runc - execute containers. Compare their UX, architecture, and impact on containerized applications.
Do you want to troubleshoot container and Kubernetes networking issues like a true expert? This is a highly practical learning path that will take you from the basics of container networking like creating a network namespace, to more complex topics like configuring a bridge network and using iptables to set up network address translation (NAT) and port forwarding.
Practice building container images, choosing the right base image, organizing multi-stage Dockerfiles, and troubleshooting common issues caused by flawed image composition.
Learn how to install Dagger and write the first modules to build, test, and deploy your application.
Start by learning how to limit process resources in Linux using cgroups—from the most basic, hands-on cgroupfs manipulation to the more convenient systemd-run command. Then, explore how Docker and Kubernetes leverage cgroups to control the resource usage of containers and pods.
Hands-on Docker on Btrfs: experiment with native snapshots, compression, and checksums; inspect setup, grow the filesystem live, and back up/restore images and containers.
A simple K3s cluster with Istio service mesh and the sample Bookinfo app deployed. The playground is a good fit for workshops, self-paced labs, and quick experimentation with Istio and service mesh fundamentals.
A sample app from https://github.com/digitalocean/kubernetes-sample-apps running on an iximiuz Labs K3s cluster.