Building container images can be both an easy and a hard problem.
Building just an image is usually as straightforward as replicating your local app build steps in a Dockerfile's RUN instructions.
Building a small, maintainable, and secure image, on the other hand, may involve lots of considerations, elaborate techniques, and domain knowledge.
And building an image that starts up quickly and behaves as expected in production is yet another level of complexity.
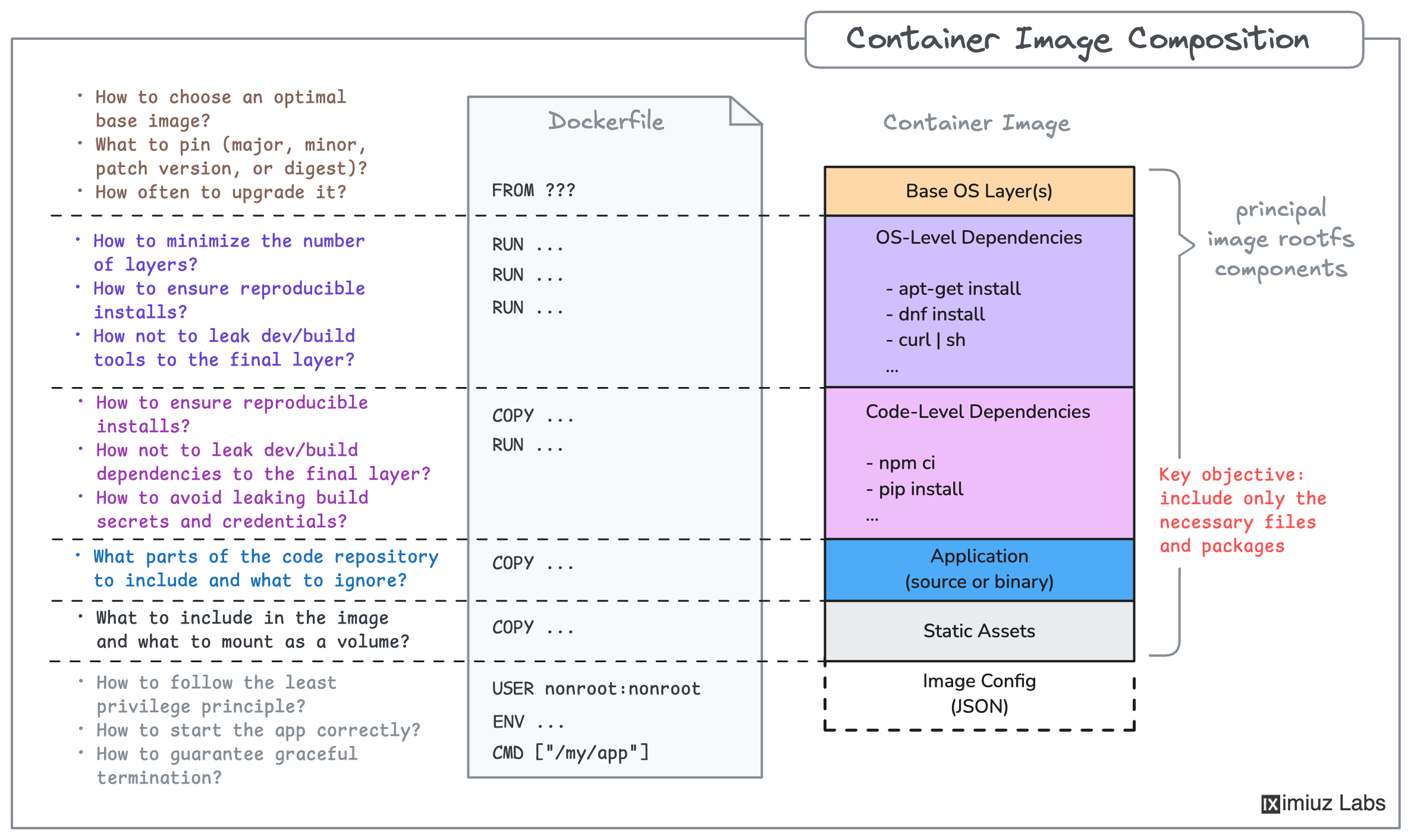
This learning path will take you from creating and pushing your very first container image, to analyzing the contents of the image, to picking an optimal base, and learning how to spot and troubleshoot runtime problems caused by flawed image composition. All of this is packed with engaging diagrams and hands-on exercises.
Happy building!
Premium Materials
Official Content Pack required
This platform is funded entirely by the community. Please consider supporting iximiuz Labs by upgrading your membership to unlock access to this and all other learning materials in the Official Collection.
Support Development