This learning path will teach you how to reproduce the most typical container networking setup: the Docker(-like) bridge network. Virtual bridge networks are extremely widespread - most Docker and Podman installations and many Kubernetes clusters (via the corresponding CNI plugin) use them to provide inter-container (or pod) communication within a single host. Understanding the underlying concepts of the bridge network is the key to efficiently troubleshooting container and Kubernetes networking issues.
You'll start with the basics, like creating a network namespace, and then move on to more complex topics, like connecting multiple network namespaces with veth pairs and a bridge device and using iptables to set up network address translation (NAT) and port publishing.
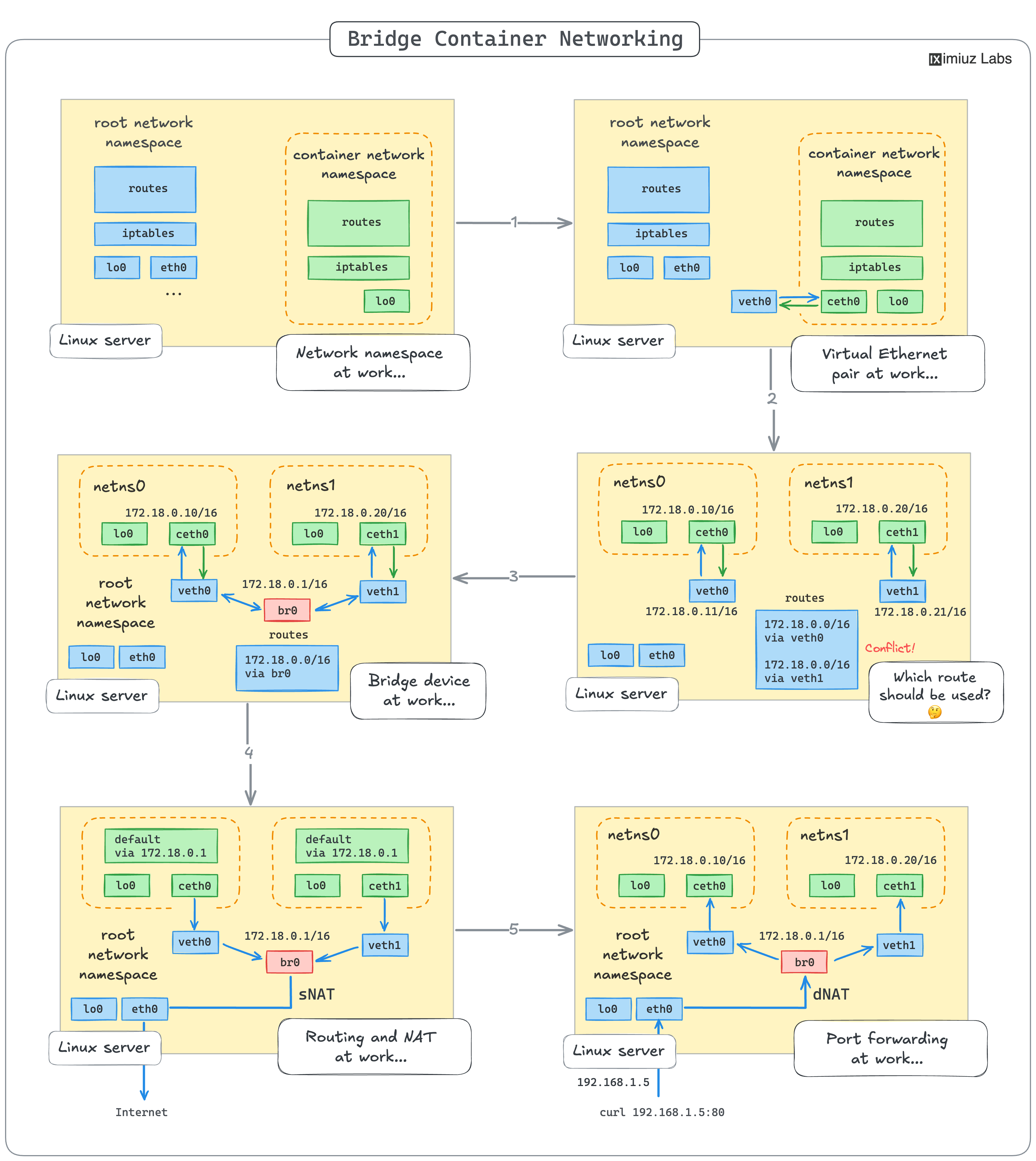
Follow along with a comprehensive tutorial, or start by solving hands-on challenges and come back to the tutorial when you get stuck. Any way you choose, by the end of this skill path, you'll gain a deep understanding of how container networking works under the hood.
Premium Materials
Official Content Pack required
This platform is funded entirely by the community. Please consider supporting iximiuz Labs by upgrading your membership to unlock access to this and all other learning materials in the Official Collection.
Support Development