What's Inside Distroless Container Images: Taking a Closer Look
GoogleContainerTools' distroless images are often mentioned as
one of the ways to produce small(er), fast(er), and secure(r) containers.
But what are these distroless images, really?
What's the difference between a container image built from a distroless base and one built FROM scratch?
Let's dive in!
Why Do We Need Distroless Images?
Container images built FROM full-blown Linux distributions like debian, ubuntu,
or their derivatives (e.g., node:lts or python:3) often come packed with tools and libraries.
While comprehensive for day-to-day tasks,
most of these components are unnecessary for typical containerized applications at runtime.
The result? Larger image sizes and more potential vulnerabilities to manage for no good technical reason.
The desire to create smaller, more secure container images by including only the essentials is natural.
The most extreme approach to achieving this minimalism is starting FROM scratch - an empty base image -
and adding only the application files and packages truly necessary for your container to function.
However, as discussed in the previous post, this approach may require significant manual effort because by default, scratch-based containers miss:
- System directories like
/tmp,/home, or/var. - CA certificates for secure connections.
- User management files (
/etc/passwd,/etc/group). - Shared libraries for dynamically linked applications.
- Time zone information.
...and possibly more.
While FROM scratch containers offer a clean start,
they are often incomplete and potentially problematic for production use without significant manual effort to fill in the gaps.
That's where distroless images come in! The GoogleContainerTools/distroless project provides prebuilt minimal base images that are as close to scratch as possible but have the necessary system files and folders in place.
The only thing you need to get started with the distroless images is to understand their hierarchy and pick the one that best fits your application's requirements.
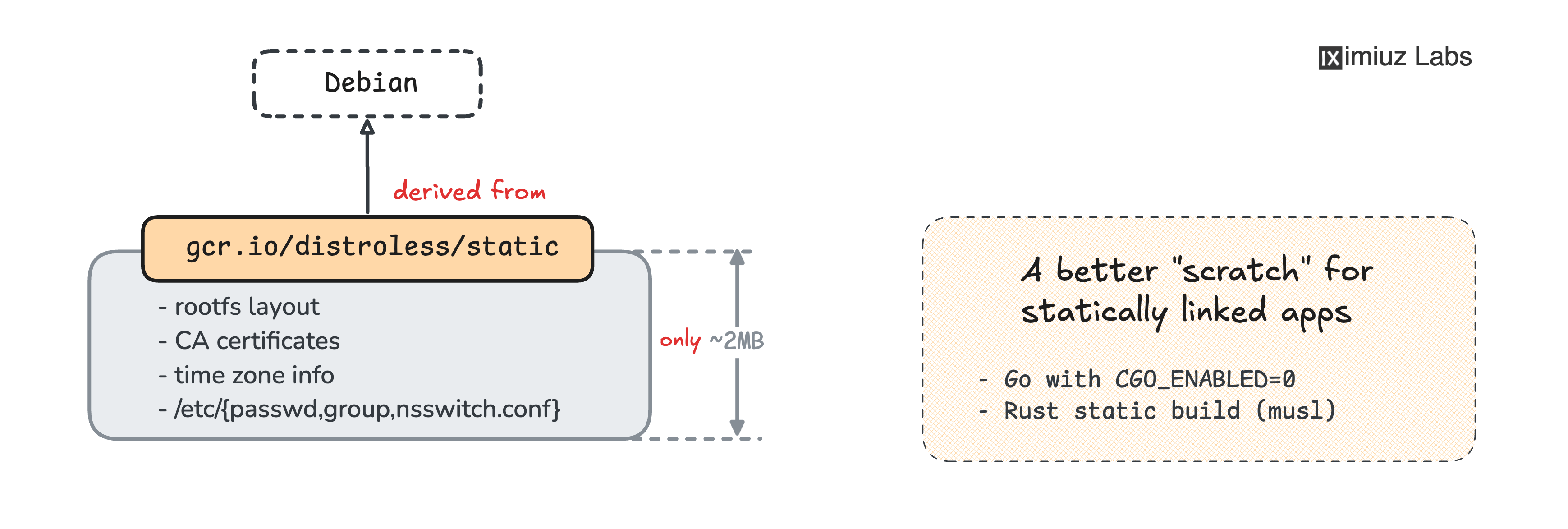
Meet the First Distroless Image: gcr.io/distroless/static
A good starting point to become familiar with the GoogleContainerTools distroless collection is
the gcr.io/distroless/static image:
docker pull gcr.io/distroless/static
docker images
REPOSITORY TAG IMAGE ID SIZE
gcr.io/distroless/static latest 5d7d2b425607 1.99MB
Inspecting its filesystem tells us that:
- It's just ~2MB (which is ~25% of the
alpineimage size 🤯) - It has a typical Linux distro directory structure inside.
- The
/etc/passwd,/etc/group, and even/etc/nsswitch.conffiles are in place. - Certificates and the time zone information are present as well.
- The image is Debian-based (so, there is a distro in the distroless image after all, but it's stripped down to the bones).
- Last but not least, the licenses seem to be preserved (but I'm not a copyright expert).
Premium Materials
Official Content Pack required
This platform is funded entirely by the community. Please consider supporting iximiuz Labs by upgrading your membership to unlock access to this and all other learning materials in the Official Collection.
Support Development