Exploring Tetragon - A Security Observability Tool for Kubernetes, Docker, and Linux
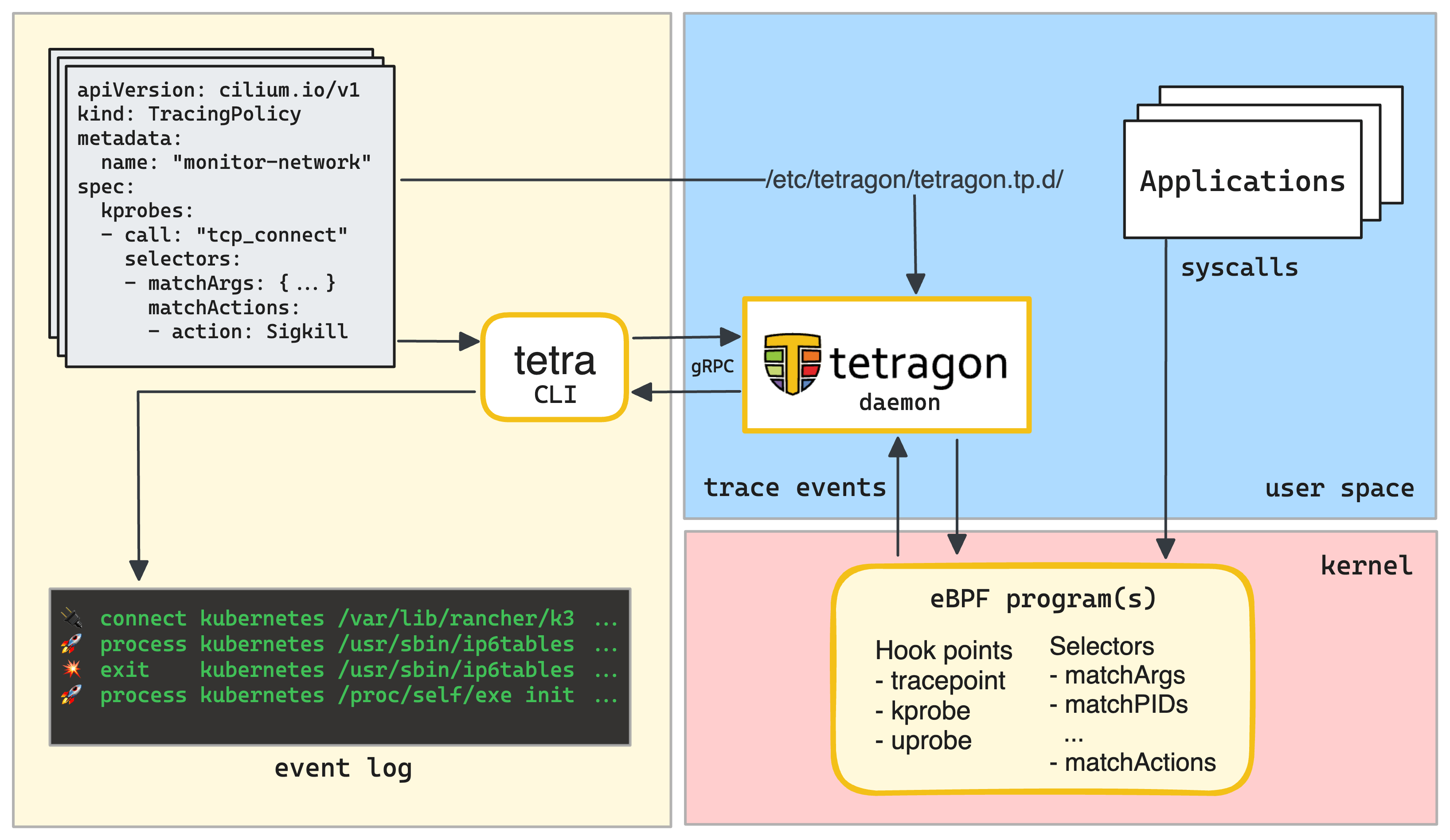
What is Tetragon, how it works, and how to use it to detect and react to security-significant events in your Kubernetes, Docker, or plain Linux environment.
Deep dives into DevOps and Server Side topics where theory blends with hands-on examples. You can try out commands from each tutorial in the attached remote playground, either from the browser or via SSH access from your local terminal — no extra setup required.
Tutorials crafted by iximiuz Labs to help you master DevOps and Server Side topics.
What is Tetragon, how it works, and how to use it to detect and react to security-significant events in your Kubernetes, Docker, or plain Linux environment.

Tutorials from outstanding independent authors proudly hosted by iximiuz Labs.
Learn how to auto-unseal works by using OpenBao'/Vault's builtin mechanism.

Learn how to get started with OpenBao/Vault by walking through the basics of initialization, unsealing, authentication, and secret management.

In this tutorial, we'll dive into the world of Docker Security, look at the attack surface of a Docker installation and show some straightforward container breakouts
Tutorials contributed by the community members sharing their knowledge and expertise.
Exploit a Kubernetes RBAC authorization bypass where nodes/proxy GET permissions allow command execution in any Pod.