Vendor produces Bill of Behaviour for their application/product
Create a Bill of Behavior - 1 Setup an app and produce benign behavior
What is a (S)BoB?
We introduce the Software “Bill of Behavior” (BoB): a vendor-supplied profile detailing known benign runtime behaviors for software, designed to be distributed directly within OCI artifacts. Generated using eBPF, a BoB codifies expected syscalls, file access patterns, network communications, and capabilities. This empowers powerful, signature-less anomaly detection, allowing end-users to infer malicious activity or tampering in third-party software without the current burden of authoring and maintaining complex, custom security rules.
It solves the problem of distributing secure-by-default and up-to-date security rules for detection and defense.

Bill of Behavior: addresses the problem of distributing secure-by-default and up-to-date security rules for detection and defense- as it is supplied inside the application-packaging
There are two primary scenarios:
1. Runtime Anomalies
This scenario covers situations where a vulnerability (CVE or ZeroDay) is present in the app and it gets exploited.
2. Supply Chain Anomalies
This scenario covers threats originating from a compromised supply chain. For example:
- The artefact is not the one from the vendor (e.g. through typosquatting, registry poisoning, unauthorized access to artefactories )
- The vendor's supply chain got otherwise compromised (i.e. the artefact is signed by the vendor, but contains malicious pieces)
Thus the software, at runtime, will exhibit some form of behavior that was unintended by its creator. This could be a beacon, a backdoor, a cryptominer, a keylogger, a rootkit, altered images for defamation or any other form of nasty.
Show your support and star ⭐️ the repo or get in contact
https://github.com/k8sstormcenter/bobctl
You can write to the authors using croedig@sba-research.org
FAQ: Will this solve all of my security issues for now and ever more?
No, a BoB s main use is that an end-user inherits a behavior profile from those that understand the software-behavior: the people who created the software.This means, that an end users profiles are secure-by-default and can be kept up-to-date automatically.
There are still many types of attacks that hide within the benign behavior or can be possible for various reasons.
Module I Objectives - Produce a Bill of Behavior as a Vendor
For this first Module, we will:
- ✅ Prepare the environment for profiling (at vendor factory-side).
- ✅ Deploy the application.
- ✅ Produce traffic to execute/trigger all known benign behavior (e.g., using a load test or Cypress tests).
- ✅ Profile (i.e.,
recordortrace) the benign behavior. - ✅ Export the profile.
The Bill of Behavior Lifecycle
Diagram: Vendor Publication of a BoB
Step 1: Lab Setup
A. Familiarize Yourself with the Lab Environment
How this lab works
Make sure you have this lab open in Chrome. Safari doesn't work.
Please hover over the bottom right corner of the code boxes, and when the Copy symbol appears, click it and Paste it into the terminal on the right (you need to activate the playground first). In Windows, you may need to right-click or configure your browser's keybindings.
You are now running a development environment of kubernetes. In Module 3, we will run on k3s, which is also real Kubernetes distribution, but from a different vendor with a rather different architecture. This is to showcase that a vendor and a consumer will likely use different infrastructure.
This Lab-Module has also been executed on kind, k3s, microk8s minikube talos and GKE. In the repo, there are BoBs produced for a variety of Kubernetes versions/architectures, and I will be adding a discussion of their differences soon.
THIS LAB IS LIVE, live rewrites could be going on.
This means, the writing on the left here can change in real time. Since you have found this lab, you likely know
Constanze, and should something happen that you have issue with, please, ping her in your usual communication channel (icmp may not be the right one 🤣)
B. Clone the Repository & Install Prerequisites
cd ~
git clone https://github.com/k8sstormcenter/bobctl.git
cd bobctl
make storage kubescape-vendor
Optional - For deploying the advanced tetragon example we need `Helmfiles`
vim ~/helmfile
chmod +x ~/helmfile
#!/bin/sh
docker run --rm --net=host \
-v "${HOME}/.kube:/root/.kube" \
-v "${HOME}/.config/helm:/root/.config/helm" \
-v "${HOME}/.minikube:/${HOME}/.minikube" \
-v "${PWD}:/wd" \
-e KUBECONFIG=/root/.kube/config \
--workdir /wd ghcr.io/helmfile/helmfile:v0.156.0 helmfile "$@"
~/helmfile init
Optional - Manually check that all Kubescape pods are `Running`
kubectl get pods -n honey -l app.kubernetes.io/instance=kubescape
You want the STATUS of all pods to be Running, like so:
laborant@dev-machine:~/honeycluster$ kubectl get pods -n honey -l app.kubernetes.io/instance=kubescape
NAME READY STATUS RESTARTS AGE
kubescape-768648957-t52hf 1/1 Running 0 8m46s
kubevuln-77897b796c-vvs24 1/1 Running 0 8m46s
node-agent-zdxlh 1/1 Running 0 8m28s
operator-546d5845-p5hxd 1/1 Running 0 8m46s
storage-6cd74486bd-6tn6l 1/1 Running 0 8m46s
Step 2: Deploy the Application
Before using real applications, we start with deploying a well-known demo** called webapp that has:
- a) Desired functionality: it pings things.
- b) Undesired functionality: it is vulnerable to injection (runtime is compromised).
- This is to mimic a CVE in your app.
- c) Tampering with the artefact: In module 2, we will additionally tamper with the artifact and make it create a backdoor (supply chain is compromised).
- This is to mimic a SupplyChain corruption between vendor and you.
The following command installs the demo webapp:
cd ~/bobctl
make helm-install-no-bob
Optional - Manually check the demo webapp is up and running
kubectl get pods -l app=webapp -o jsonpath='{range .items[*]}{.status.conditions[?(@.type=="Ready")].status}{"\n"}{end}'
If you get True, proceed.
**: credit belongs entirely to the original authors
Step 3: Generate Traffic of Benign Behavior
Benign (adjective) bi-ˈnīn
- Benignity (noun) bi-ˈnig-nə-tē
- Benignly (adverb) bi-ˈnīn-lē
Definitions/SYNONYMS:
- Of a mild type or character that does not threaten health or life. HARMLESS.
- Of a gentle disposition: GRACIOUS.
- Showing kindness and gentleness. FAVORABLE, WHOLESOME.
We assume that the full set of benign behaviour consists of the webapp performing a few pings internally to our cluster. Thus, we simply make the app execute a few such pings. This is not representative for all possible things that the webapp could do, but let's keep it simple for starters.
In a production use-case, you d probably run various test-suites instead of a manual REST call.
Manually creating benign traffic
Let's test the Desired functionality: which in this case translates to a single ping
cd ~/bobctl
make fwd
curl localhost:8080/ping.php?ip=172.16.0.2
If that works, open a new tab new terminal and let it loop:
while true; do curl localhost:8080/ping.php?ip=172.16.0.2; sleep 10; done
Once you are sure it executed the ping a few times, please CTRL+C the loop and switch back to the original dev-machine tab
Step 4: Packaging the benign traffic tests into a software supply chain framework (such as Helm)
Ideally, the vendor packages all tests that produce benign traffic together with the application, sign-it and ship it.
Packaging requirements
- Composable Signature adding subsequent layers must be signable without invalidating any previous signatures.
- Transparency tests use existing ecosystem mechanisms for minimal user friction
Concrete Example
- Helm Chart test hooks
- Other standard automation frameworks
For the webapp, we implemented a simple hook (which is essentially the same ping-test as above)
cd ~/bobctl
make helm-test
helm test for webapp
apiVersion: v1
kind: Pod
metadata:
name: "{{ include "mywebapp.fullname" . }}-test-connection"
labels:
{{- include "mywebapp.labels" . | nindent 4 }}
kubescape.io/ignore: "true"
annotations:
"helm.sh/hook": test
"helm.sh/hook-delete-policy": hook-succeeded,hook-failed
spec:
restartPolicy: Never
containers:
- name: curl
image: curlimages/curl:8.7.1
command:
- /bin/sh
- -c
- |
set -ex
SERVICE="{{ include "mywebapp.fullname" . }}"
NAMESPACE="{{ .Release.Namespace }}"
PORT="{{ .Values.service.port }}"
TARGET_IP="{{ .Values.bob.targetIp }}"
URL="${SERVICE}.${NAMESPACE}.svc.cluster.local:${PORT}/ping.php?ip=${TARGET_IP}"
RESPONSE=$(curl -s "$URL")
echo "$RESPONSE"
echo "$RESPONSE" | grep -q "Ping results for ${TARGET_IP}"
echo "$RESPONSE" | grep -q "${TARGET_IP} ping statistics"
Deployment is ready. Running Helm tests...
helm test webapp -n webapp
NAME: webapp
LAST DEPLOYED: Thu Jul 17 11:35:26 2025
NAMESPACE: webapp
STATUS: deployed
REVISION: 1
TEST SUITE: webapp-mywebapp-test-connection
Last Started: Thu Jul 17 11:57:57 2025
Last Completed: Thu Jul 17 11:58:02 2025
Phase: Succeeded
NOTES:
Your webapp-mywebapp application is now deployed.
WIP: We understand that this webapp is extremely simplistic and in a later Module will show how we
would approach multi-container pods, statefulsets and operators.
Future research will be on proofing additivity and composibility in general terms.
(Thanks Ben for pointing this out)
You are done here ✅ and you may proceed to the next unit, please. Leave the tabs on the right open.
Summary so far
- We installed the application for which to create the bob
- We selected
benigntraffic to trigger the application's desired behavior - We packaged the app and the traffic into an artefact (we used a
helm chartand included ahelm test)
Profiling with Kubescape
Now, we are still the vendor and have the webapp deployed on our cluster.
We are producing benign traffic that triggers all known behavior of our webapp (and in later Modules, the other apps)

Kubescape Space PandaBear, according to legend, its name is Mo - all credit goes to Team Kubescape/Armosec
Introduction to Kubescape/Nodeagent: Viktor's video may serve as great Overview and Introduction
We have installed kubescape, it will help us use eBPF/Inspector Gadget in a hands-off manner via its nodeagent-component. So we'll use a config that only installs the runtime-behavior module producing an output that an end-user can directly consume, without having to deal with ebpf or kernel interna directly.
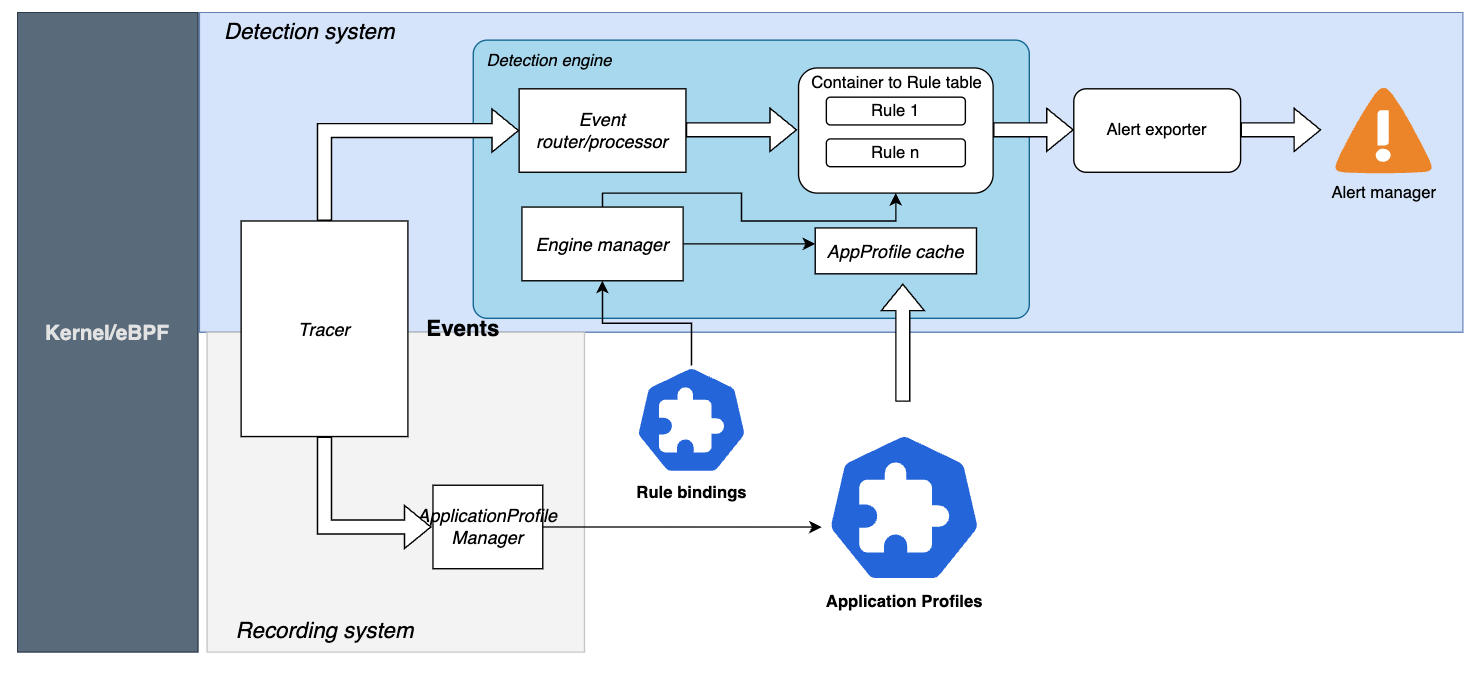
Kubescape Architecture for RunTime Security: The NodeAgent will be sniffing the container for a specified amount of time and update the recorded behavior in a CRD. Once completed, it serves as base for anomaly detection which emits Alerts (if desired)
The Goal: Capture an ApplicationProfile for the full lifecycle of the application
In order to produce a correct ApplicationProfile, that will serve as base for our BoB, we need to be aware of some config parameters.
Also, we need to understand from which part of the lifecycle (init vs up-and-running), some profile entries are coming.
So, how is KubeScape configured, what are the rules?
We use KubeScape Nodeagent as profiler (however there are other means to create such profiles) and we need to understand what exactly we are recording.
Especially the UpdatePeriods and Exclusions must be correct otherwise the Profile will be incorrect.
The settings are in a ConfigMap and CustomResourceDefinition named RuntimeRuleAlertBinding
kubectl describe cm -n honey ks-cloud-config
kubectl get RuntimeRuleAlertBinding all-rules-all-pods -o yaml
Rule Bindings - beware of the exclusions in the rules
apiVersion: kubescape.io/v1
kind: RuntimeRuleAlertBinding
metadata:
annotations:
meta.helm.sh/release-name: kubescape
meta.helm.sh/release-namespace: honey
creationTimestamp: "2025-07-09T16:01:57Z"
generation: 2
labels:
app: node-agent
app.kubernetes.io/component: node-agent
app.kubernetes.io/instance: kubescape
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/name: kubescape-operator
app.kubernetes.io/part-of: kubescape
app.kubernetes.io/version: 1.28.0
helm.sh/chart: kubescape-operator-1.28.0
kubescape.io/ignore: "true"
tier: ks-control-plane
name: all-rules-all-pods
resourceVersion: "1609"
uid: 4dddea53-82a0-4709-bab5-3cf20bfe501f
spec:
namespaceSelector:
matchExpressions:
- key: kubernetes.io/metadata.name
operator: NotIn
values:
- kubescape
- kube-system
- cert-manager
- openebs
- kube-public
- kube-flannel
- kube-node-lease
- kubeconfig
- gmp-system
- gmp-public
- honey
- storm
- lightening
rules:
- ruleName: Unexpected process launched
- parameters:
includePrefixes: #I ve configured NO exclusions here
- /proc
- /run/secrets/kubernetes.io/serviceaccount
- /var/run/secrets/kubernetes.io/serviceaccount
- /tmp
- /etc
- /var/spool/cron/
- /var/log/
- /var/run/
- /dev/shm/
- /run/
- /var/www/
- /var/lib/docker/
- /opt/
- /usr/local/
- /app/
- /.dockerenv
- /proc/self/environ
- /var/lib/kubelet/
- /etc/cni/net.d/
- /var/run/secrets/kubernetes.io/
- /var/run/secrets/kubernetes.io/serviceaccount/
- /run/containerd/
- /run/flannel/
- /run/calico/
ruleName: Unexpected file access
- ruleName: Unexpected system call
- ruleName: Unexpected capability used
- ruleName: Unexpected domain request
- ruleName: Unexpected Service Account Token Access
- ruleName: Kubernetes Client Executed
- ruleName: Exec from malicious source
- ruleName: Kernel Module Load
- ruleName: Exec Binary Not In Base Image
- ruleName: Fileless Execution
- ruleName: XMR Crypto Mining Detection
- ruleName: Exec from mount
- ruleName: Crypto Mining Related Port Communication
- ruleName: Crypto Mining Domain Communication
- ruleName: Read Environment Variables from procfs
- ruleName: eBPF Program Load
- ruleName: Symlink Created Over Sensitive File
- ruleName: Unexpected Sensitive File Access
- ruleName: Hardlink Created Over Sensitive File
- ruleName: Exec to pod
- ruleName: Port forward
- ruleName: Malicious Ptrace Usage
- ruleName: Cross-Site Scripting (XSS) Attempt
- ruleName: SQL Injection Attempt
- ruleName: Server-Side Request Forgery Attack Attempt
- ruleName: Remote File Inclusion Attack Attempt
- ruleName: Local File Inclusion Attempt
- ruleName: XML External Entity Attack Attempt
- ruleName: Server-Side Template Injection Attack
- ruleName: Command Injection Attempt
- ruleName: Unexpected Exec Source
- ruleName: Unexpected Open Source
- ruleName: Unexpected Symlink Source
- ruleName: Unexpected Hardlink Source
- ruleName: Unexpected io_uring Operation Detected
- ruleName: ReDoS Attack
- ruleName: Prototype Pollution Attack
- ruleName: Execution of base64 Encoded Command
- ruleName: Execution of interpreter command
- ruleName: Code Sharing Site Access
- ruleName: Web Application File Write Access
- ruleName: Cron Job File Created or Modified
- ruleName: Hidden File Created
- ruleName: Reverse Shell Patterens Detected
- ruleName: Unauthorized IMDS Connection Attempt
- ruleName: Credentials Detection Attempts
- ruleName: HTTP Request Smuggling Attempt
Couple of other important settings to be aware of that govern the anomaly detection and the
learning duration. i.e. how long we have to generate a benign behaviour profile.
kubectl get cm node-agent -n honey -o yaml
Configuration of NodeAgent
apiVersion: v1
data:
config.json: |
{
"applicationProfileServiceEnabled": true,
"prometheusExporterEnabled": false,
"runtimeDetectionEnabled": true,
"httpDetectionEnabled": true,
"networkServiceEnabled": true,
"malwareDetectionEnabled": false,
"hostMalwareSensorEnabled": false,
"hostNetworkSensorEnabled": false,
"nodeProfileServiceEnabled": false,
"networkStreamingEnabled": false,
"maxImageSize": 5.36870912e+09,
"maxSBOMSize": 2.097152e+07,
"sbomGenerationEnabled": true,
"enableEmbeddedSBOMs": false,
"seccompServiceEnabled": true,
"initialDelay": "10m",
"updateDataPeriod": "5m",
"nodeProfileInterval": "10m",
"networkStreamingInterval": "2m",
"maxSniffingTimePerContainer": "20m",
"excludeNamespaces": "kubescape,kube-system,kube-public,kube-node-lease,kubeconfig,gmp-system,gmp-public,honey,storm,lightening,cert-manager,openebs,kube-flannel,ingress-nginx,olm,pl,px-operator",
"excludeLabels":null,
"exporters": {
"alertManagerExporterUrls":[],
"stdoutExporter":true,
"syslogExporterURL": ""
},
"excludeJsonPaths":null,
"ruleCooldown": {
"ruleCooldownDuration": "0h",
"ruleCooldownAfterCount": 1e+09,
"ruleCooldownOnProfileFailure": false,
"ruleCooldownMaxSize": 20000
}
}
kind: ConfigMap
metadata:
annotations:
meta.helm.sh/release-name: kubescape
meta.helm.sh/release-namespace: honey
creationTimestamp: "2025-07-09T16:01:57Z"
labels:
app: node-agent
app.kubernetes.io/component: node-agent
app.kubernetes.io/instance: kubescape
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/name: kubescape-operator
app.kubernetes.io/part-of: kubescape
app.kubernetes.io/version: 1.28.0
helm.sh/chart: kubescape-operator-1.28.0
kubescape.io/ignore: "true"
kubescape.io/tier: core
tier: ks-control-plane
name: node-agent
namespace: honey
Show me the ApplicationProfiles !
kubectl get applicationprofile -A
NAMESPACE NAME CREATED AT
webapp replicaset-webapp-mywebapp-67965968bb 2025-04-16T13:58:34Z
export rs=$(kubectl get replicaset -n webapp -o jsonpath='{.items[0].metadata.name}')
kubectl describe applicationprofile replicaset-$rs -n webapp
For production, definitely wait til the profile states completed, in this lab and if you only follow along with our ping-app, it doesn't matter.
What really matters is that all tests and benign traffic must have been executed against the application before you use the profile, else the profile will detect the benign behavior as an anomaly and classify it as malicious when we use it later.
I chose to put the default learning time to 20min, which is appropriate for proper apps with a handful of tests. While this is way too long for the ping-app, the profile content can already be used as long as you know, you ve executed all the tests.
You can use this lab for your own app: create another namespace and execute your usual tests or usage for your own app. You will get additional applicationprofiles after 20min
in their respective namespace. You should adapt the maxLearningPeriod and the learningPeriod in the values.yaml such that all tests that create benign traffic or trigger benign functionality fit into the maxLearningPeriod.
How to find if the status of the profile is completed
Also, in the crd annotation, you will find the status completed now.
kubectl describe applicationprofile replicaset-webapp-xxx
...
...
Annotations: kubescape.io/status: completed
Now, we must save this above file onto disk:
kubectl get applicationprofile replicaset-$rs -n webapp -o yaml > app-profile-webapp.yaml
Great job!
References
- Kubescape Nodeagent
Documentation on Runtime threat detection as part of the Kubescape Operator
Create the Bill Of Behaviour - Hello Bob
Lets look in more detail at the profile that recorded this benign behaviour , yours should be different
cat app-profile-webapp.yaml
You ll recognize different blocks, and our next step will be about parametrizing this profile. So, have a look at the sections:
Spec:
Architectures: # very clearly the profile will differ across architectures
amd64
Containers:
Capabilities: # pods in kubernetes are made of multiple containers, this lists all capabilities that the pod used
NET_RAW
SETUID
...
Endpoints: # network inside the cluster and to external endpoints
Direction: inbound
Endpoint: :32132/ping.php
Headers:
Host:
172.16.0.2:32132
Internal: false
Methods:
GET
Execs:
Args:
/bin/ping
-c
4
172.16.0.2
Path: /bin/ping
Args:
/bin/sh
-c
ping -c 4 172.16.0.2
Path: /bin/sh
Image ID: ghcr.io/k8sstormcenter/webapp@sha256:e323014e...
Image Tag: ghcr.io/k8sstormcenter/webapp:latest
Name: mywebapp-app
Opens:
Flags:
O_RDONLY
Path: /var/www/html/ping.php
Flags:
O_CLOEXEC
O_RDONLY
Path: /lib/x86_64-linux-gnu/libc-2.31.so
...
Syscalls:
accept4
capset
chdir
clone
...
Does this translate across different cluster types?
Glad you asked :)
It does ... somewhat. The syscalls differ generally speaking even when staying on the same architecture.
You'll further notice, that the network connections are a bit different, this has to do with how the port-forward was done.
The other obvious difference is that on arm some calls are named differently, such as O_DIRECT instead of O_DIRECTORY. Furthermore, on arm there are fewer syscalls, 77 vs 86.
The parameters that matter (hypothesis)
My working hypothesis is, that in order to translate between systems, we need to account for:
| OS | Glibc Version | Kernel Version | Kubernetes Distro | Kubernetes Version | Architecture |- For network endpoints: that it will not be generally possible to account for all different ways/headers/methods etc and that there will be edge cases that the end-user needs to investigate
- unclear is, in howfar
|LSM| runtimeclass| containerruntime| CNI|and similar parameters play into it, and whether the difference is significant.
Immediate conclusion:
We need to parametrize/template for network-connections and for (uuids in) filepaths. For syscalls create supersets and/or comment in an advisory.
For architecture, we require multi-arch builds.
Before we look at various sidecars and multi-container-pods. Lets stay with this simply ping webapp that does very little, and compare its profiles across selected clusters and archs**
**NB: this comparison was an early one, before I understood what to control for. I'll soon replace the list with the uptodate parameter study in the repo.
apiVersion: spdx.softwarecomposition.kubescape.io/v1beta1
kind: ApplicationProfile
metadata:
name: NEEDSTOMATCH
namespace: NEEDSTOMATCH
spec:
architectures:
- amd64
containers:
- capabilities:
- DAC_OVERRIDE
- SETGID
- SETUID
execs:
- args:
- /bin/mkdir
- -p
- /var/lock/apache2
path: /bin/mkdir
- args:
- /usr/local/bin/docker-php-entrypoint
- apache2-foreground
path: /usr/local/bin/docker-php-entrypoint
- args:
- /usr/bin/dirname
- /var/log/apache2
path: /usr/bin/dirname
- args:
- /bin/mkdir
- -p
- /var/run/apache2
path: /bin/mkdir
- args:
- /usr/bin/dirname
- /var/lock/apache2
opens:
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_authz_host.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/auth_basic.load
...
identifiedCallStacks: null
imageID: ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b
imageTag: ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b
name: ping-app
syscalls:
- accept4
- access
- arch_prctl
- bind
- brk
...
If you'd like to inspect the full (and rather long) profiles, please unfold the below box. Otherwise, we'll now proceed to parametrize the profile, such that you (in the role of vendor) may package the profile as bob
Full profiles compared across 5 environments
apiVersion: spdx.softwarecomposition.kubescape.io/v1beta1
kind: ApplicationProfile
metadata:
name: NEEDSTOMATCH
namespace: NEEDSTOMATCH
spec:
architectures:
- amd64
containers:
- capabilities:
- DAC_OVERRIDE
- SETGID
- SETUID
execs:
- args:
- /bin/mkdir
- -p
- /var/lock/apache2
path: /bin/mkdir
- args:
- /usr/local/bin/docker-php-entrypoint
- apache2-foreground
path: /usr/local/bin/docker-php-entrypoint
- args:
- /usr/bin/dirname
- /var/log/apache2
path: /usr/bin/dirname
- args:
- /bin/mkdir
- -p
- /var/run/apache2
path: /bin/mkdir
- args:
- /usr/bin/dirname
- /var/lock/apache2
path: /usr/bin/dirname
- args:
- /bin/mkdir
- -p
- /var/log/apache2
path: /bin/mkdir
- args:
- /usr/bin/dirname
- /var/run/apache2
path: /usr/bin/dirname
- args:
- /usr/sbin/apache2
- -DFOREGROUND
path: /usr/sbin/apache2
- args:
- /usr/local/bin/apache2-foreground
path: /usr/local/bin/apache2-foreground
- args:
- /bin/rm
- -f
- /var/run/apache2/apache2.pid
path: /bin/rm
imageID: docker.io/amitschendel/ping-app@sha256:99fe0f297bbaeca1896219486de8d777fa46bd5b0cabe8488de77405149c524d
imageTag: docker.io/amitschendel/ping-app:latest
name: ping-app
opens:
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_authz_host.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/auth_basic.load
- flags:
- O_RDONLY
path: /usr/local/etc/php/conf.d/docker-php-ext-sodium.ini
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/authn_core.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/conf-available/security.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libkrb5support.so.0.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_reqtimeout.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/ports.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/local/lib/php/extensions/no-debug-non-zts-20190902/sodium.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/env.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libkrb5.so.3.3
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libxml2.so.2.9.10
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libresolv-2.31.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libnghttp2.so.14.20.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libbrotlicommon.so.1.0.9
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libsqlite3.so.0.8.6
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/hosts
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libcrypto.so.1.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libreadline.so.8.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libcrypt.so.1.1.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/mime.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/liblzma.so.5.2.5
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/mpm_prefork.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libldap_r-2.4.so.2.11.5
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/negotiation.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_negotiation.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/nsswitch.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libm-2.31.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libsodium.so.23.3.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/negotiation.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libonig.so.5.1.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/php7.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libgpg-error.so.0.29.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_access_compat.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /proc/⋯/mounts
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/authz_user.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/mime.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libpthread-2.31.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/dir.conf
- flags:
- O_CLOEXEC
- O_DIRECTORY
- O_NONBLOCK
- O_RDONLY
path: /etc/apache2/conf-enabled
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/host.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libgcrypt.so.20.2.8
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/status.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/share/zoneinfo/Etc/UTC
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/deflate.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_filter.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libselinux.so.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libbrotlidec.so.1.0.9
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libidn2.so.0.3.7
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libpcre.so.3.13.3
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/deflate.load
- flags:
- O_RDONLY
path: /proc/sys/kernel/ngroups_max
- flags:
- O_RDONLY
path: /usr/local/bin/docker-php-entrypoint
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_status.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libgssapi_krb5.so.2.2
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libdl-2.31.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libnss_files-2.31.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/setenvif.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/access_compat.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/reqtimeout.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/ld.so.cache
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_authz_user.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/librtmp.so.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libgcc_s.so.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libstdc++.so.6.0.28
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libcurl.so.4.7.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libgnutls.so.30.29.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libcap.so.2.44
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/liblber-2.4.so.2.11.5
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libssh2.so.1.0.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libaprutil-1.so.0.6.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_alias.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/authn_file.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_mpm_prefork.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libk5crypto.so.3.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libexpat.so.1.6.12
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/autoindex.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_env.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_deflate.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/group
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libtinfo.so.6.2
- flags:
- O_RDONLY
path: /usr/local/bin/apache2-foreground
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/conf-available/other-vhosts-access-log.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/authz_core.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/authz_host.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/mpm_prefork.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/gai.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/sites-available/000-default.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libp11-kit.so.0.3.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_authz_core.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/alias.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_autoindex.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libnettle.so.8.4
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libicudata.so.67.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libapr-1.so.0.7.0
- flags:
- O_CLOEXEC
- O_DIRECTORY
- O_NONBLOCK
- O_RDONLY
path: /etc/apache2/sites-enabled
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libgmp.so.10.4.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libunistring.so.2.1.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/setenvif.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/resolv.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libicuuc.so.67.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libhogweed.so.6.4
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libsasl2.so.2.0.25
- flags:
- O_RDONLY
path: /etc/apache2/envvars
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/alias.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_authn_file.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_setenvif.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/dir.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libpcre2-8.so.0.10.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libc-2.31.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/conf-available/localized-error-pages.conf
- flags:
- O_RDONLY
path: /var/www/html/ping.php
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/passwd
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libuuid.so.1.3.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_mime.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libpsl.so.5.3.2
- flags:
- O_CREAT
- O_EXCL
- O_RDWR
path: /run/apache2/apache2.pid.RS0yKf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libssl.so.1.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libcom_err.so.2.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/libphp7.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_authn_core.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libargon2.so.1
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libtasn1.so.6.6.0
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/filter.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libz.so.1.2.11
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/conf-available/docker-php.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/autoindex.load
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/conf-available/charset.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/status.load
- flags:
- O_RDONLY
path: /etc/ssl/openssl.cnf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /proc/⋯/task/1/fd
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/conf-available/serve-cgi-bin.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_auth_basic.so
- flags:
- O_CLOEXEC
- O_DIRECTORY
- O_NONBLOCK
- O_RDONLY
path: /usr/local/etc/php/conf.d
- flags:
- O_CLOEXEC
- O_RDONLY
path: /lib/x86_64-linux-gnu/libkeyutils.so.1.9
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/apache2.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/apache2/mods-available/reqtimeout.conf
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/x86_64-linux-gnu/libffi.so.7.1.0
- flags:
- O_CLOEXEC
- O_DIRECTORY
- O_NONBLOCK
- O_RDONLY
path: /etc/apache2/mods-enabled
- flags:
- O_CLOEXEC
- O_RDONLY
path: /etc/mime.types
- flags:
- O_CLOEXEC
- O_RDONLY
path: /usr/lib/apache2/modules/mod_dir.so
- flags:
- O_CLOEXEC
- O_RDONLY
path: /proc/filesystems
seccompProfile:
spec:
defaultAction: ""
syscalls:
- accept4
- access
- arch_prctl
- bind
- brk
- capget
- capset
- chdir
- chmod
- clone
- close
- close_range
- connect
- dup2
- dup3
- epoll_create1
- epoll_ctl
- epoll_pwait
- execve
- exit
- exit_group
- faccessat2
- fcntl
- fstat
- fstatfs
- futex
- getcwd
- getdents64
- getegid
- geteuid
- getgid
- getpgrp
- getpid
- getppid
- getrandom
- getsockname
- getsockopt
- gettid
- getuid
- ioctl
- listen
- lseek
- lstat
- mkdir
- mmap
- mprotect
- munmap
- nanosleep
- newfstatat
- openat
- pipe
- pipe2
- poll
- prctl
- prlimit64
- read
- recvfrom
- recvmsg
- rename
- rt_sigaction
- rt_sigprocmask
- rt_sigreturn
- select
- sendto
- set_robust_list
- set_tid_address
- setgid
- setgroups
- setitimer
- setsockopt
- setuid
- shutdown
- sigaltstack
- socket
- stat
- statfs
- sysinfo
- times
- tkill
- umask
- uname
- unlinkat
- vfork
- wait4
- write
- writev
So, to create a Bill of Behavior, first make sure the installation and positive testing works properly (for Constanze, this is manual). Afterwards, automate the process and superset the bobs content.
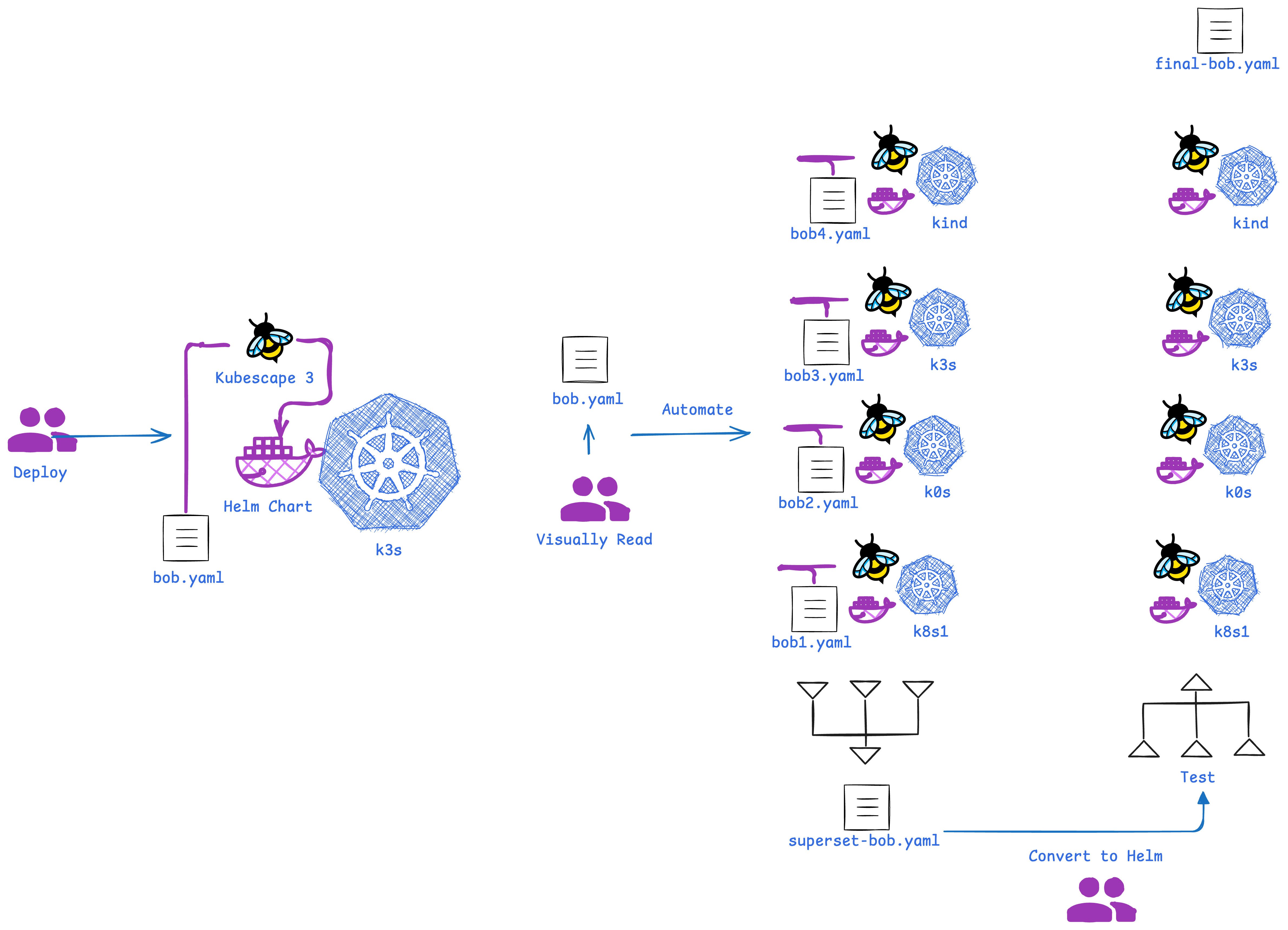
There is a script in the repo:
cat ~/bobctl/testdata/superset.sh
References
- OCI Image Specification
The specification governing container images, used as the foundation for artifact transport. - binfmt_misc & QEMU Emulation
Documentation on enabling cross-architecture emulation for binary execution in container.
Glossary
- Software Bill of Behaviour (SBOB) or (BoB)
A Software Bill of Behaviors (SBoB) is an emerging concept aimed at capturing and documenting the runtime behavior of software components to enhance system security and threat detection.
SuperSet the Application Profile
This section will be described in full detail in the Automation Chapter. Here's the gist:
Rationale: Syscalls and a few other things differ across systems
Assuming we stay on one architecture, we run the profiling across a large parameter space e.g. using a matrix build.
git clone if you havnt previously
cd ~
git clone https://github.com/k8sstormcenter/bobctl.git
cd bobctl
Creating 35 Profiles in this github matrix build (WIP are those in red which are constantly added and fixed)
So, for each setup that we add to the huge matrix, we first need to make it work and then extract the application profile. To find such a set, navigate to
ls /home/laborant/bobctl/testdata/parameterstudy/redis/auto2
cd ~/bobctl
Now, we have a script that parses all profiles and supersets them:
git checkout 44-bobctl-can-take-applicationprofile-and-parametrize-it-into-a-helm-syntax
make superset-bob INPUT_DIR=testdata/parameterstudy/redis/auto2 OUTPUT_FILE=testdata/parameterstudy/redis/superset-bob.yaml
cat testdata/parameterstudy/redis/superset-bob.yaml
Parametrize the Application Profile
🚧 WIP: Now we'll prepare the Application Profile such that it can be packaged for distribution.
Looking at the Redis supersetted appProfile from the previous step, there is very little we need to parametrize
execs:
- args:
- /bin/bash
- -c
- /opt/bitnami/scripts/start-scripts/start-master.sh
path: /bin/bash
- args:
- /opt/bitnami/redis/bin/redis-server
- --port
- "6379" #this is a port that is usually controlled via a helm-chart value
- --protected-mode
- "no"
- --include
- /opt/bitnami/redis/etc/redis.conf
- --include
- /opt/bitnami/redis/etc/master.conf
path: /opt/bitnami/redis/bin/redis-server
Now, it should become obvious why you need to be knowledgeable of the software, its internal workings and the way the configuration is abstracted. Cause you simply need to know, which parts make sense to be overridden or overrideable.
Here is where a vendor might write a script that automates the translation of such settings into their preferred template language
execs:
- args:
- /bin/bash
- -c
- /opt/bitnami/scripts/start-scripts/start-master.sh
path: /bin/bash
- args:
- /opt/bitnami/redis/bin/redis-server
- --port
- "{{ .Values.service.port }}" #HELM syntax here
- --protected-mode
- "no"
- --include
- /opt/bitnami/redis/etc/redis.conf
- --include
- /opt/bitnami/redis/etc/master.conf
path: /opt/bitnami/redis/bin/redis-server
Seperating out the Enforcement part
Additionally, we know that the capabilities are only used by the executables. While enforcing syscalls is generally a bad idea, as they dont translate well across systems, executable paths are predetermined. The capabilities with which they run are also similar (there are cases when OS calls are offloaded to the underlying node, that they can differ)
- capabilities:
- DAC_OVERRIDE
- DAC_READ_SEARCH
- NET_ADMIN
🧙♂️ You shall not pass!
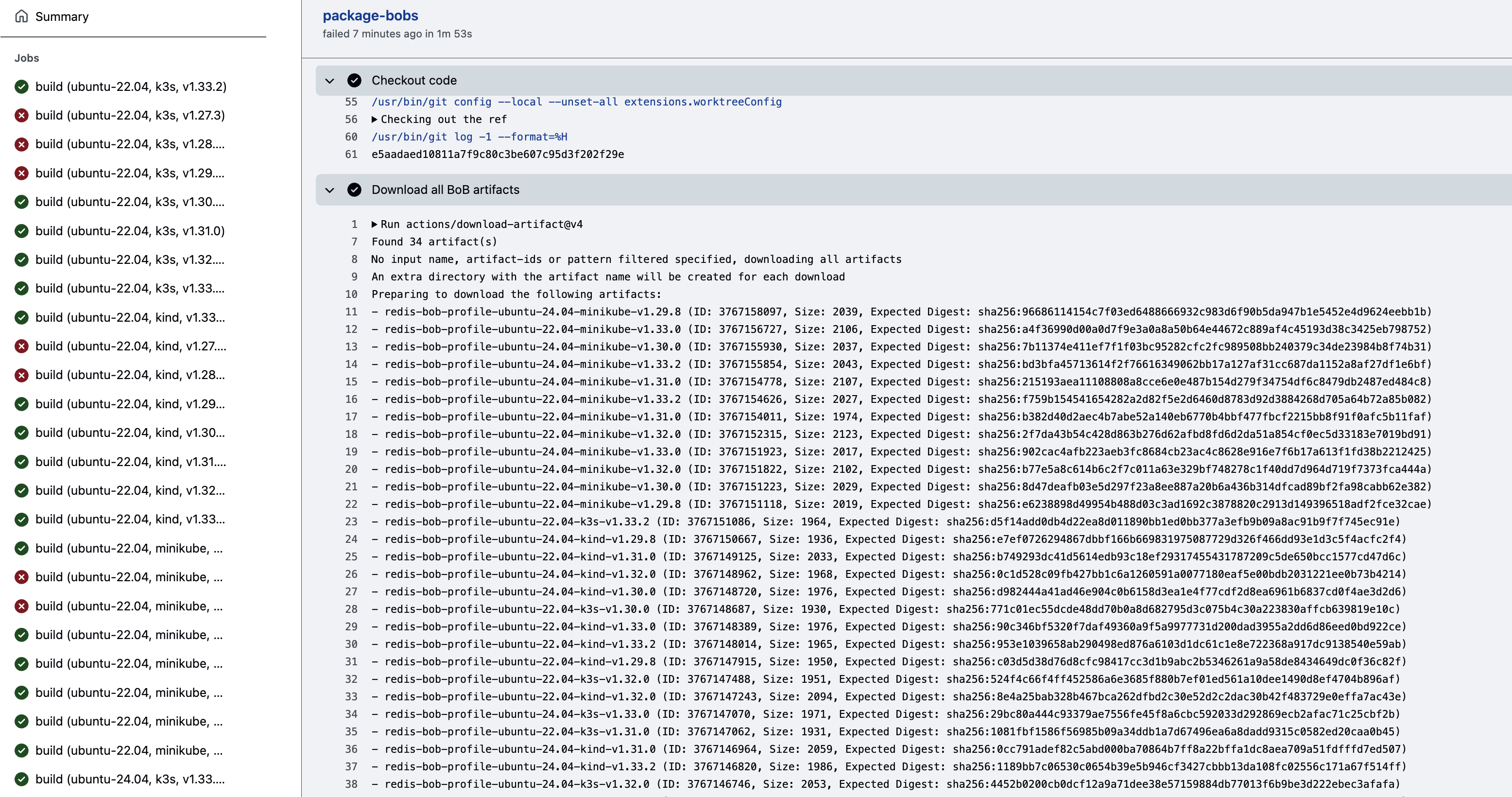
🚧 Work in progress... Please, consider upgrading your account to Premium to help us finish this content faster.Verify the anomaly detection
We now verify that kubescape can use the previously recorded profile and detect anything else (that was NOT previously recorded as benign ) as an anomaly.
1) Normal anomalies: A malicious runtime behaviour by executing a simple injection like so:
in Tab 1 tail the logs again
kubectl logs -n honey -l app=node-agent -f -c node-agent
and in Tab 2, let's do something malicious
make attack
This will execute a variety of command injections, like the following one
curl localhost:8080/ping.php?ip=172.16.0.2\;ls
In the other tab, you should now see unexpected things:
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/bin/ls"],"exec":"/bin/ls","retval":0},"infectedPID":6972,"severity":5,"size":"4.1 kB","timestamp":"2025-05-14T09:41:34.973055288Z","trace":{}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"honeycluster","containerName":"ping-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"default","containerID":"2b3c4de694b3e5668c920cea48db530892eda11c4984552a7457b7f5af701d9c","podName":"webapp-d87cdd796-4ltvq","podNamespace":"default","podLabels":{"app":"webapp","pod-template-hash":"d87cdd796"},"workloadName":"webapp","workloadNamespace":"default","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":6950,"cmdline":"/bin/sh -c ping -c 4 172.16.0.2;ls","comm":"sh","ppid":5180,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"ls␟6972":{"pid":6972,"cmdline":"/bin/ls ","comm":"ls","ppid":6950,"pcomm":"sh","hardlink":"/bin/ls","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/ls"}}},"containerID":"2b3c4de694b3e5668c920cea48db530892eda11c4984552a7457b7f5af701d9c"},"event":{"runtime":{"runtimeName":"containerd","containerId":"2b3c4de694b3e5668c920cea48db530892eda11c4984552a7457b7f5af701d9c","containerName":"ping-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"default","podName":"webapp-d87cdd796-4ltvq","podLabels":{"app":"webapp","pod-template-hash":"d87cdd796"},"containerName":"ping-app","owner":{}},"timestamp":1747215694973055288,"type":"normal"},"level":"error","message":"Unexpected process launched: /bin/ls","msg":"Unexpected process launched","time":"2025-05-14T09:41:34Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected file access","arguments":{"flags":["O_RDONLY","O_NONBLOCK","O_DIRECTORY","O_CLOEXEC"],"path":"/var/www/html"},"infectedPID":6972,"severity":1,"timestamp":"2025-05-14T09:41:34.975867565Z","trace":{}},"CloudMetadata":null,"RuleID":"R0002","RuntimeK8sDetails":{"clusterName":"honeycluster","containerName":"ping-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"default","containerID":"2b3c4de694b3e5668c920cea48db530892eda11c4984552a7457b7f5af701d9c","podName":"webapp-d87cdd796-4ltvq","podNamespace":"default","workloadName":"webapp","workloadNamespace":"default","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":6950,"cmdline":"/bin/sh -c ping -c 4 172.16.0.2;ls","comm":"sh","ppid":5180,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"ls␟6972":{"pid":6972,"cmdline":"/bin/ls ","comm":"ls","ppid":6950,"pcomm":"sh","hardlink":"/bin/ls","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/ls"}}},"containerID":"2b3c4de694b3e5668c920cea48db530892eda11c4984552a7457b7f5af701d9c"},"event":{"runtime":{"runtimeName":"containerd","containerId":"2b3c4de694b3e5668c920cea48db530892eda11c4984552a7457b7f5af701d9c","containerName":"ping-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"default","podName":"webapp-d87cdd796-4ltvq","podLabels":{"app":"webapp","pod-template-hash":"d87cdd796"},"containerName":"ping-app","owner":{}},"timestamp":1747215694975867565,"type":"normal"},"level":"error","message":"Unexpected file access: /var/www/html with flags O_RDONLY,O_NONBLOCK,O_DIRECTORY,O_CLOEXEC","msg":"Unexpected file access","time":"2025-05-14T09:41:34Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"sendmmsg"},"infectedPID":15899,"md5Hash":"4e79f11b07df8f72e945e0e3b3587177","sha1Hash":"b361a04dcb3086d0ecf960d3acaa776c62f03a55","severity":1,"size":"730 kB","timestamp":"2025-07-07T21:22:12.648682466Z","trace":{},"uniqueID":"b8ae38884cb701d21b2862f2cdbee24e","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":15899,"cmdline":"apache2 -DFOREGROUND","comm":"apache2","ppid":15845,"pcomm":"containerd-shim","uid":0,"gid":0,"startTime":"0001-01-01T00:00:00Z","cwd":"/var/www/html","path":"/usr/sbin/apache2"},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"k8s":{"node":"cplane-01","namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923332648682466,"type":"normal"},"level":"error","message":"Unexpected system call: sendmmsg","msg":"Unexpected system call","time":"2025-07-07T21:22:12Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"socketpair"},"infectedPID":15899,"md5Hash":"4e79f11b07df8f72e945e0e3b3587177","sha1Hash":"b361a04dcb3086d0ecf960d3acaa776c62f03a55","severity":1,"size":"730 kB","timestamp":"2025-07-07T21:22:12.655726956Z","trace":{},"uniqueID":"668c081933ba8b63ab41bf2f74ba5c69","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":15899,"cmdline":"apache2 -DFOREGROUND","comm":"apache2","ppid":15845,"pcomm":"containerd-shim","uid":0,"gid":0,"startTime":"0001-01-01T00:00:00Z","cwd":"/var/www/html","path":"/usr/sbin/apache2"},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"k8s":{"node":"cplane-01","namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923332655726956,"type":"normal"},"level":"error","message":"Unexpected system call: socketpair","msg":"Unexpected system call","time":"2025-07-07T21:22:12Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected domain request","arguments":{"addresses":["216.58.210.174"],"domain":"google.com.","port":50015,"protocol":"UDP"},"infectedPID":20611,"severity":5,"size":"4.1 kB","timestamp":"2025-07-07T21:22:10.417464343Z","trace":{},"uniqueID":"0b80141cea771029450509ea63514032","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":1}},"CloudMetadata":null,"RuleID":"R0005","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":20589,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;curl google.com","comm":"sh","ppid":15922,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"curl␟20611":{"pid":20611,"cmdline":"/usr/bin/curl google.com","comm":"curl","ppid":20589,"pcomm":"sh","hardlink":"/usr/bin/curl","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/usr/bin/curl"}}},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923330417464343,"type":"normal"},"level":"error","message":"Unexpected domain communication: google.com. from: mywebapp-app","msg":"Unexpected domain request","time":"2025-07-07T21:22:10Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"getpeername"},"infectedPID":15899,"md5Hash":"4e79f11b07df8f72e945e0e3b3587177","sha1Hash":"b361a04dcb3086d0ecf960d3acaa776c62f03a55","severity":1,"size":"730 kB","timestamp":"2025-07-07T21:22:12.639434336Z","trace":{},"uniqueID":"69bbdde26311ca1a112c3449cc03d209","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":15899,"cmdline":"apache2 -DFOREGROUND","comm":"apache2","ppid":15845,"pcomm":"containerd-shim","uid":0,"gid":0,"startTime":"0001-01-01T00:00:00Z","cwd":"/var/www/html","path":"/usr/sbin/apache2"},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"k8s":{"node":"cplane-01","namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923332639434336,"type":"normal"},"level":"error","message":"Unexpected system call: getpeername","msg":"Unexpected system call","time":"2025-07-07T21:22:12Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/usr/bin/curl","google.com"],"exec":"/usr/bin/curl","retval":0},"infectedPID":20611,"severity":5,"size":"4.1 kB","timestamp":"2025-07-07T21:22:10.396395121Z","trace":{},"uniqueID":"10eb3203d2094782c9a560b1207a9c66","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":20589,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;curl google.com","comm":"sh","ppid":15922,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"curl␟20611":{"pid":20611,"cmdline":"/usr/bin/curl google.com","comm":"curl","ppid":20589,"pcomm":"sh","hardlink":"/usr/bin/curl","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/usr/bin/curl"}}},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923330396395121,"type":"normal"},"level":"error","message":"Unexpected process launched: /usr/bin/curl","msg":"Unexpected process launched","time":"2025-07-07T21:22:10Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected Service Account Token Access","arguments":{"flags":["O_RDONLY"],"path":"/run/secrets/kubernetes.io/serviceaccount/..2025_07_07_21_05_56.676258237/token"},"infectedPID":20588,"severity":8,"timestamp":"2025-07-07T21:22:07.355497979Z","trace":{},"uniqueID":"d077f244def8a70e5ea758bd8352fcd8","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0006","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":20586,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"sh","ppid":16216,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟20588":{"pid":20588,"cmdline":"/bin/cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"cat","ppid":20586,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923327355497979,"type":"normal"},"level":"error","message":"Unexpected access to service account token: /run/secrets/kubernetes.io/serviceaccount/..2025_07_07_21_05_56.676258237/token with flags: O_RDONLY","msg":"Unexpected Service Account Token Access","time":"2025-07-07T21:22:07Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected file access","arguments":{"flags":["O_RDONLY"],"path":"/run/secrets/kubernetes.io/serviceaccount/..2025_07_07_21_05_56.676258237/token"},"infectedPID":20588,"severity":1,"timestamp":"2025-07-07T21:22:07.355497979Z","trace":{},"uniqueID":"6fa0673cb27a4829df52779bb1d42923","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0002","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":20586,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"sh","ppid":16216,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟20588":{"pid":20588,"cmdline":"/bin/cat /run/secrets/kubernetes.io/serviceaccount/token","comm":"cat","ppid":20586,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923327355497979,"type":"normal"},"level":"error","message":"Unexpected file access: /run/secrets/kubernetes.io/serviceaccount/..2025_07_07_21_05_56.676258237/token with flags O_RDONLY","msg":"Unexpected file access","time":"2025-07-07T21:22:07Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected system call","arguments":{"syscall":"fadvise64"},"infectedPID":15899,"md5Hash":"4e79f11b07df8f72e945e0e3b3587177","sha1Hash":"b361a04dcb3086d0ecf960d3acaa776c62f03a55","severity":1,"size":"730 kB","timestamp":"2025-07-07T21:22:02.638550612Z","trace":{},"uniqueID":"840a89954c4149cca50949888cfdb6a6","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0003","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":15899,"cmdline":"apache2 -DFOREGROUND","comm":"apache2","ppid":15845,"pcomm":"containerd-shim","uid":0,"gid":0,"startTime":"0001-01-01T00:00:00Z","cwd":"/var/www/html","path":"/usr/sbin/apache2"},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"k8s":{"node":"cplane-01","namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923322638550612,"type":"normal"},"level":"error","message":"Unexpected system call: fadvise64","msg":"Unexpected system call","time":"2025-07-07T21:22:02Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected file access","arguments":{"flags":["O_RDONLY"],"path":"/var/www/html/index.html"},"infectedPID":20581,"severity":1,"timestamp":"2025-07-07T21:22:04.332009145Z","trace":{},"uniqueID":"df2808e2d1f9a406d267ce3037697a3f","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0002","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":20543,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat index.html","comm":"sh","ppid":15926,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟20581":{"pid":20581,"cmdline":"/bin/cat index.html","comm":"cat","ppid":20543,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923324332009145,"type":"normal"},"level":"error","message":"Unexpected file access: /var/www/html/index.html with flags O_RDONLY","msg":"Unexpected file access","time":"2025-07-07T21:22:04Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected file access","arguments":{"flags":["O_RDONLY","O_NONBLOCK","O_DIRECTORY","O_CLOEXEC"],"path":"/var/www/html"},"infectedPID":20503,"severity":1,"timestamp":"2025-07-07T21:21:58.287348855Z","trace":{},"uniqueID":"6a62049e8c5629b76f4f2f6d32e17cb0","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0002","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":20495,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;ls","comm":"sh","ppid":15924,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"ls␟20503":{"pid":20503,"cmdline":"/bin/ls ","comm":"ls","ppid":20495,"pcomm":"sh","hardlink":"/bin/ls","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/ls"}}},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923318287348855,"type":"normal"},"level":"error","message":"Unexpected file access: /var/www/html with flags O_RDONLY,O_NONBLOCK,O_DIRECTORY,O_CLOEXEC","msg":"Unexpected file access","time":"2025-07-07T21:21:58Z"}
{"BaseRuntimeMetadata":{"alertName":"Unexpected process launched","arguments":{"args":["/bin/cat","/proc/self/mounts"],"exec":"/bin/cat","retval":0},"infectedPID":20527,"severity":5,"size":"4.1 kB","timestamp":"2025-07-07T21:22:01.312624103Z","trace":{},"uniqueID":"86a130a79323f10e54cf35ed94f7df9a","profileMetadata":{"status":"completed","completion":"complete","name":"replicaset-webapp-mywebapp-67965968bb","failOnProfile":true,"type":0}},"CloudMetadata":null,"RuleID":"R0001","RuntimeK8sDetails":{"clusterName":"bobexample","containerName":"mywebapp-app","hostNetwork":false,"image":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","imageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb","namespace":"webapp","containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","podName":"webapp-mywebapp-67965968bb-76d6g","podNamespace":"webapp","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"workloadName":"webapp-mywebapp","workloadNamespace":"webapp","workloadKind":"Deployment"},"RuntimeProcessDetails":{"processTree":{"pid":20504,"cmdline":"/bin/sh -c ping -c 4 1.1.1.1;cat /proc/self/mounts","comm":"sh","ppid":15925,"pcomm":"apache2","hardlink":"/bin/dash","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/dash","childrenMap":{"cat␟20527":{"pid":20527,"cmdline":"/bin/cat /proc/self/mounts","comm":"cat","ppid":20504,"pcomm":"sh","hardlink":"/bin/cat","uid":33,"gid":33,"startTime":"0001-01-01T00:00:00Z","upperLayer":false,"cwd":"/var/www/html","path":"/bin/cat"}}},"containerID":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35"},"event":{"runtime":{"runtimeName":"containerd","containerId":"48ce40eaf1f1d19a1b2125ecefdffe5de5c28910a6c24739309322a6228dad35","containerName":"mywebapp-app","containerImageName":"ghcr.io/k8sstormcenter/webapp@sha256:e323014ec9befb76bc551f8cc3bf158120150e2e277bae11844c2da6c56c0a2b","containerImageDigest":"sha256:c622cf306b94e8a6e7cfd718f048015e033614170f19228d8beee23a0ccc57bb"},"k8s":{"namespace":"webapp","podName":"webapp-mywebapp-67965968bb-76d6g","podLabels":{"app.kubernetes.io/instance":"webapp","app.kubernetes.io/name":"mywebapp","pod-template-hash":"67965968bb"},"containerName":"mywebapp-app","owner":{}},"timestamp":1751923321312624103,"type":"normal"},"level":"error","message":"Unexpected process launched: /bin/cat","msg":"Unexpected process launched","time":"2025-07-07T21:22:01Z"}
Level up your Server Side game — Join 20,000 engineers who receive insightful learning materials straight to their inbox