eBPF Beginner Skill Path
Introduction
Running your first “Hello, eBPF!” program is usually straightforward—just a few lines of C and an eBPF loader (libbpf)—but understanding what happens under the hood takes some time and patience. Concepts like maps, the verifier, and various eBPF tools/frameworks might sound complex at first, yet they form the foundation of every production-grade eBPF application.
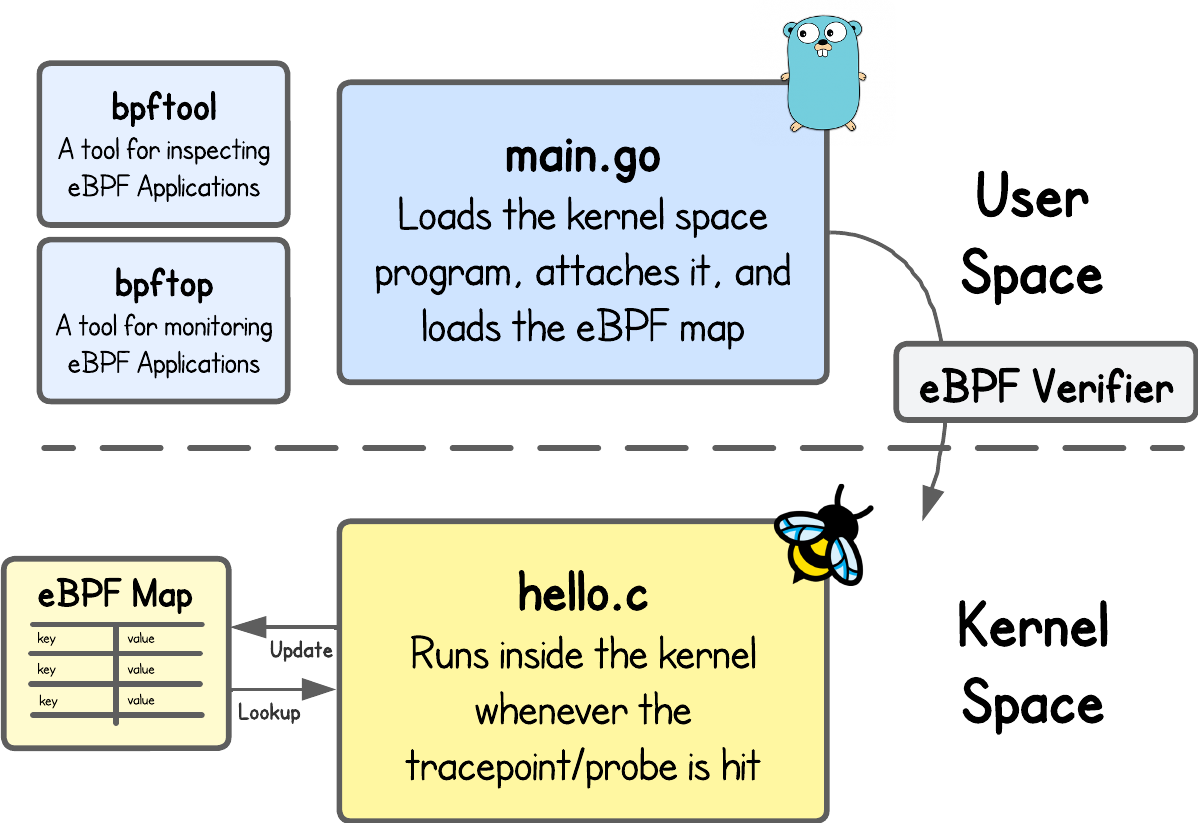
This learning path will take you from writing and loading your very first eBPF program, to storing and sharing data in eBPF maps, to inspecting and monitoring your programs with bpftool and bpftop. You’ll also learn how the eBPF verifier keeps your programs safe to run in the kernel. Finally, you’ll get to test your knowledge through an eBPF challenge designed specifically for beginners.
Hands-on, practical, and focused on fundamentals—this path will give you the confidence to start building your own eBPF tools.
Happy 🐝-ing!
Your First eBPF Program
Loading tutorial...
When you start writing your first eBPF program, there are many moving parts to get right — where to write the program, how to load it into the kernel, where to attach it, and how to debug it, just to name a few. Without understanding these basics, it’s easy to feel lost as things become more complex.
In this tutorial, you’ll run a pre-written eBPF program and explore how it’s loaded and hooked into the kernel. By the end, you’ll have a clear understanding of the key components that make eBPF work — giving you the confidence to start writing your own programs.
Your First eBPF Map
Loading tutorial...
Writing and loading a “Hello, World!” eBPF program might seem easy, but that can only take you so far. At some point, you’ll need a way to store information inside the kernel — to track events, maintain counters, or share state between eBPF programs and user space. That’s exactly what eBPF maps are for.
In this tutorial, you’ll learn how to use eBPF maps to store and manage data inside the kernel, and how to inspect them with bpftool.
Inspecting and Monitoring eBPF Programs
Loading tutorial...
As you start building eBPF programs, it’s easy to lose track of what’s actually running inside the kernel. You might have multiple programs and maps loaded, but without the right tools, understanding their state and behavior can feel like a black box.
In this tutorial, you’ll get hands-on with two powerful tools — bpftool and bpftop that let you inspect, analyze, and monitor your eBPF programs, giving you full visibility into how they operate and perform inside the kernel.
How the Kernel Safely Runs eBPF Programs
Loading tutorial...
Running code inside the Linux kernel may sound risky — a single bug could crash the entire system. Yet eBPF manages to do this safely, allowing developers to extend kernel functionality without compromising stability. But how is that possible?
In this tutorial, you’ll learn how the verifier keeps eBPF safe, why it’s such a critical part of the ecosystem, and how to handle different verification errors.
Challenge Yourself
Last but not least — put your knowledge to the test and take it into the wild.