Enable Internet Access for a Private Network with a NAT Gateway
You've just joined the ops team of Project Umbrella, a tiny start-up that's been prototyping sensor firmware on an air-gapped lab network. Their two lab servers - node-01 and node-02 - sit on an RFC 1918 subnet and can't reach the outside world, which has become a blocker for package installs, software updates, and pulling container images.
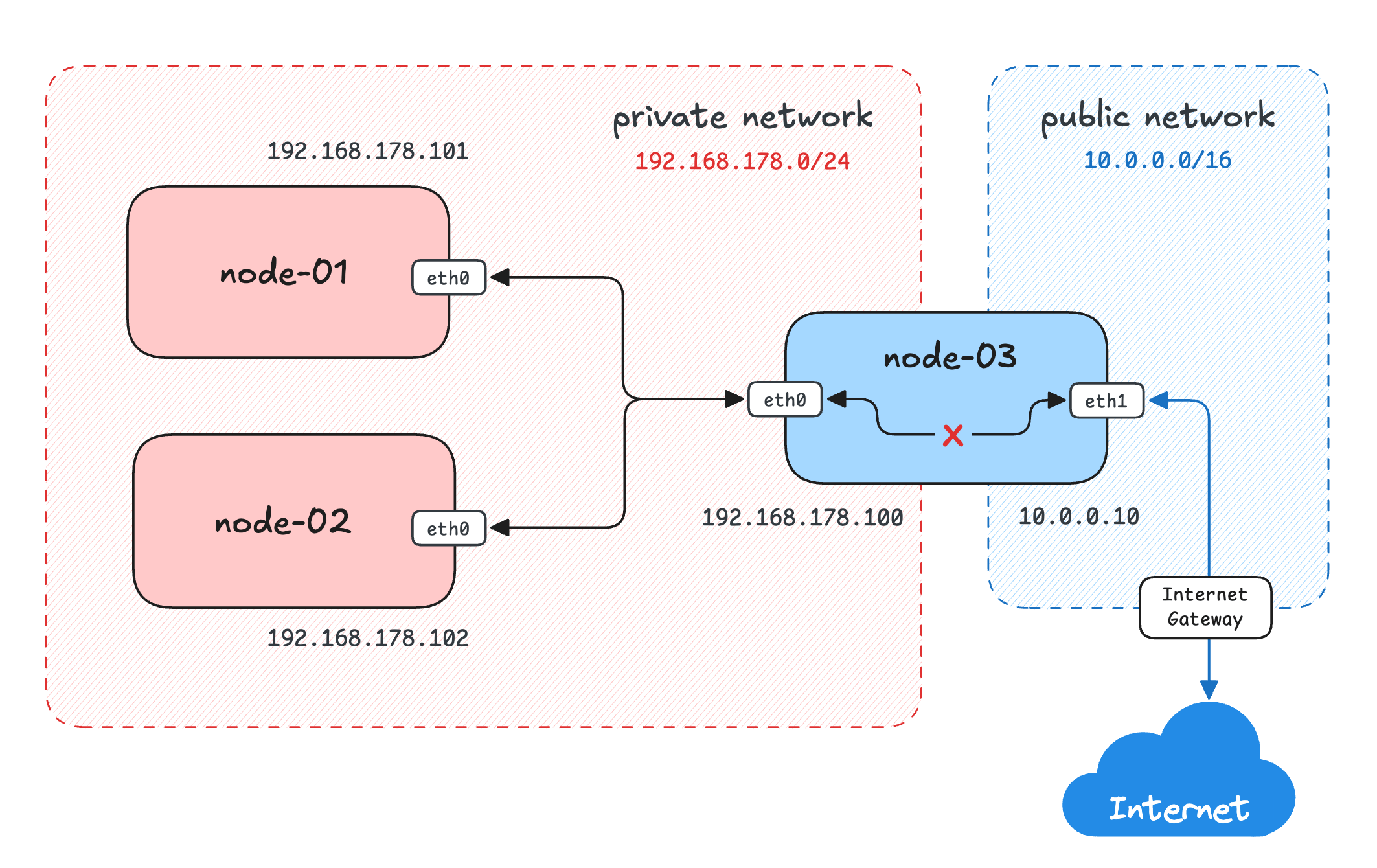
A third host - node-03 - was racked yesterday. It has:
eth0on the same private lab network (IP192.168.178.100/24)eth1plugged into the office "public" network (IP10.0.0.10/16)
Your mission: Turn node-03 into a NAT gateway and wire up the routing so the private hosts can reach the Internet while remaining invisible from the outside.
The current setup is as follows:
- node-01: Private network only (
192.168.178.101/24) - node-02: Private network only (
192.168.178.102/24) - node-03: Dual-homed gateway (
192.168.178.100/24+10.0.0.10/16)
Configure the default route on node-01 to point to the (future) NAT gateway:
Hint 1 - Adding a default route (theory)
The node-01 machine needs to know where to send traffic destined for networks outside the private subnet.
Configure a default route that points to the 192.168.178.100 IP address of node-03.
Use the ip route add command. Run man ip-route to see the syntax.
Hint 2 - Adding a default route (practice)
Reading the man page isn't fun? Then try solving this routing challenge first.
Similarly, configure the default route on node-02 to point to the same NAT gateway:
Hint 3 - Default Route on node-02
Just like node-01, node-02 also needs a default route pointing to the NAT gateway. The same command applies here since both nodes are on the same private network.
Enable IP forwarding on the gateway node-03:
Hint 4 - Enable IP Forwarding
By default, Linux systems don't forward packets between network interfaces of the same machine. The gateway needs to be explicitly configured to forward packets from the private network to the public network.
Configure NAT masquerading on the gateway node-03:
Hint 5 - Why IP forwarding is not enough
Turning on IP forwarding lets Linux pass packets between eth0 (private) and eth1 (public) interfaces of the gateway node-03,
but it doesn’t solve the address problem.
A packet that leaves node-01 still carries the source IP 192.168.178.101.
The upstream router on the public network will drop any reply to that RFC 1918 address because it is not globally routable.
To make the conversation work you must replace the source IP addresses of the packets leaving the private network with the gateway's IP address on the way out and restore the original (private) source address on the way back. This is called (source) Network Address Translation (NAT).
Hint 6 - NAT Masquerading
Network Address Translation (NAT), or more specifically, source network address translation (sNAT) rewrites the source IP addresses of packets leaving the private network so they appear to come from the gateway's public IP address.
Here's what you want to happen when node-01 (192.168.178.101) makes a request to 8.8.8.8:
- node-01 sends:
192.168.178.101:12345 → 8.8.8.8:53 - node-03 (gateway) rewrites:
10.0.0.10:54321 → 8.8.8.8:53(masquerading) - Response comes back:
8.8.8.8:53 → 10.0.0.10:54321 - Gateway translates back:
8.8.8.8:53 → 192.168.178.101:12345
To add the masquerading rule, you will need to use the iptables command on the gateway machine.
Time to test Internet connectivity from node-01 and node-02:
Why This Matters
Whether you're granting Internet access to a home-lab subnet, letting a small office share one public IP address, or enabling outbound traffic from a private cloud VPC, the job often comes down to configuring a lightweight Linux host to forward packets and perform network address translation.
By the end of this challenge you'll have touched the three pillars of a DIY gateway:
- Routing (so packets know where to go)
- Forwarding (so the kernel actually moves them between interfaces)
- Network Address Translation (so private RFC 1918 space is safely hidden behind a public IP)